
Mobile in enterprise is transforming how we interact with information, connect with our office networks, and organize our working lives.
We have become so reliant on mobile devices to drive our entertainment, social, and knowledge networks that they naturally begin to intertwine with our work lives, but at what cost?
What are the challenges?
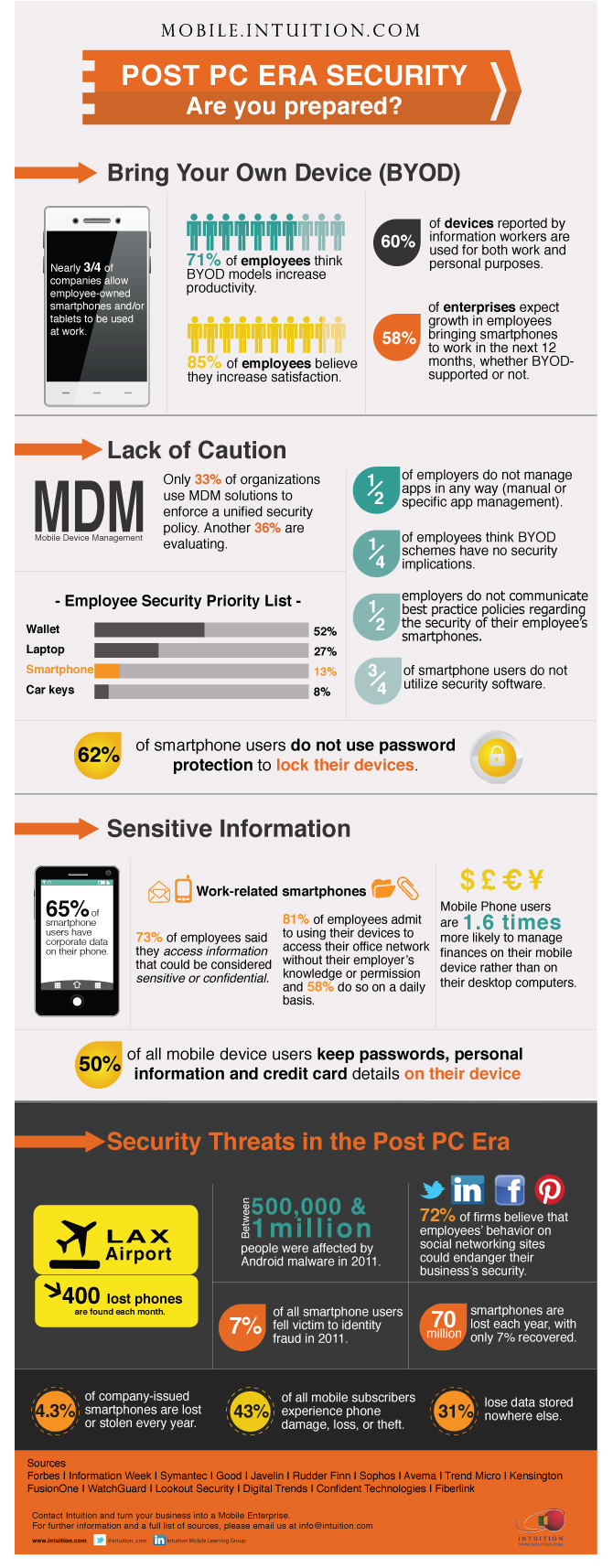
In a recent survey from Symantec, 72 percent of firms believe that employees’ behaviour on social networking sites could endanger their business’s security. And 91 percent of respondents to a survey said their company allows employees to use their work-related smartphones for personal use as well.
While this demonstrates the utility, practicality, and flexibility of using mobile devices to conduct business (often on demand and on the move), it is also an indication of both the immediate and impending challenges for organizations to ensure they have an adequate infrastructure in place to deal effectively with new security threats as they occur across several platforms.
Indeed, few organizations have a mobile security agenda in place, and many organizations are still unaware of the security threat posed by unrestricted smartphones. Only 51% of employees said their employer has communicated policies and/or best practices to them regarding the security of their smartphones.
The key concern of any organization is ensuring that sensitive information is subject to robust on-device security and encryption. In an era of multi-platform usage in enterprise, the issue of general information security becomes central to an organization’s ability to remain secure while maintaining healthy levels of productivity by avoiding excessive network downtime.
Around 73 percent of employees said they use their work-related smartphones to access information that could be considered sensitive or confidential.
What does this mean for organizations?
Half of all organizations are not prepared for the influx of personal mobile devices leading to serious headaches for IT departments struggling to devise an appropriate security policy.
- Organizations are unable to monitor or control employees’ work-related activities on their smartphone, increasing the risk of sensitive company data being compromised.
- Many organizations do not have user authentication policies on their employees’ mobile devices allowing unauthorized access to potentially sensitive company data.
- Organizations are unable to react to a security compromise or suspicious user behaviour by locking down a mobile device and wiping the contents if required.
- Employees are taking their smartphones overseas with them and potentially incurring huge roaming charges as organizations are unable to restrict access through roaming controls.
What is the solution?
Your organization needs to be sure that sensitive data is both secure and protected from unauthorized access. Your organization also need to be sure that your data are safe on servers, safe in transit and safe on your employees’ mobile devices. Here is what we advise in order to effectively ring-fence your data.
Currently, more than half (52 percent) of all employers have no app management system in place to manage apps on their employees’ smartphone.
- Security policy: Devise a clear and comprehensive mobile security policy. In an era where more and more employees are bringing their own smartphone to work, it is crucial that you have a clear policy in place to effectively deal with a multitude of devices with different approaches to security.
- Closed-loop system: Help your mobile enterprise flourish and keep your sensitive data secure by enforcing a closed loop system. What does this mean? It means requiring user authentication in order to access enterprise data on a mobile device. It means allowing users access only to the information they should have access to and preventing unauthorized sharing of that information.
- Track access: Be in control of data security by being able to track access with information due dates and expiration dates.
- Remote lock: Respond instantly to security risks by remotely locking access to data on specific employee devices or removing access entirely if an employee goes rogue or if the mobile device is lost or stolen.
- Roaming controls: Install roaming controls on employee smartphones in order to avoid the crippling cost of escalating mobile data charges incurred when overseas.
Are you a smartphone user?
So how do you combat these growing threats to your private data stored on your smartphone? Well, for starters, you had better make sure that you are staying one step ahead of the game by pre-empting security threats. Here are five things you can do right now to instantly boost security on your smartphone:
- Update: Always ensure your mobile firmware is up-to-date. This means regularly checking for updates to ensure that you have the latest security features to avoid exposing your device to security flaws that hackers are just waiting to exploit.
- Use an antivirus program: If your smartphone runs Android, Google’s open source mobile operating system, ensure that you have an antivirus app such as AVG installed to guard against potential malware lurking behind seemingly harmless apps.
- Use a PIN lock: Ensure your Smartphone has a PIN lock to access the phone and another PIN to access the home screen after your phone has been lying idle for a couple of minutes.
- Stay vigilant: Avoid clicking links in an anonymous text message or from an unreliable source within your mobile browser. Such attacks from seemingly harmless sources are on the rise as hackers target smartphones containing valuable personal and financial data.
- Be wary of apps: Only install apps from reputable sources. This is especially applicable to users of rooted phones or Android devices where apps may be installed from any source. Make sure that you only download apps from an approved marketplace and only after reviewing user comments and ratings for the app.
 Kris Swanson is the chief commercial officer for Intuition Technology. Intuition Technology enables organizations to rapidly create, securely deliver, and seamlessly track courses, surveys, assessments, and other content across most mobile devices and tablets. Intuition Technology has successfully delivered over 150 mobile learning solutions since 2006.
Kris Swanson is the chief commercial officer for Intuition Technology. Intuition Technology enables organizations to rapidly create, securely deliver, and seamlessly track courses, surveys, assessments, and other content across most mobile devices and tablets. Intuition Technology has successfully delivered over 150 mobile learning solutions since 2006.
Image courtesy of David Hammonds, Shutterstock


