Updated with new information on what Google is doing to combat the threat – July 5
Mobile security company Bluebox said today that it recently discovered a vulnerability in Android that makes any Android device released in the last four years vulnerable to hackers who can read your data, get your passwords, and control any function of your phone, including sending texts, making phone calls, or turning on the camera.
That’s almost 900 million Android devices globally.
“A Trojan application … has the ability to read arbitrary application data on the device (email, SMS messages, documents, etc.), retrieve all stored account & service passwords,” Bluebox CTO Jeff Forristal posted. “It can essentially take over the normal functioning of the phone and control any function.”
The vulnerability is due to “discrepancies” in how Android apps are approved and verified, Bluebox says, allowing hackers to tamper with application code without changing the app’s cryptographic signatures. That means that an app — any app — that looks perfectly safe and legitimate to an app store, a device, an engineer, or a user actually could actually have malicious code embedded within it.
Forristal said the details of the bug were disclosed to Google back in February and that Google has “notified their device partners.”
The problem, however, is that because of Android’s fragmented nature and the fact that device manufacturers and mobile carriers release Android updates sporadically if at all, many Android devices are not running the latest software and cannot be easily user-updated.
Forristal puts it diplomatically:
“The availability of these updates will widely vary depending upon the manufacturer and model in question.”
If an attacker successfully gains control of an Android device — and Bluebox will be revealing technical details of the vulnerability at hacker conference Black Hat USA 2013 in late July — the hacker essentially gains control of all permissions on the phone or tablet.
That’s a disaster for users, because many Android users, particularly those in Asian and Eastern countries, use the 500+ independent Android app stores that have little or no authentication or verification procedures to ensure passing through their services are legit, forming a perfect opportunity for unscrupulous and technically-inclined thieves and spies to gain control of your phone.
I asked Google for comment and received a this terse response from a Google representative:
We aren’t commenting.
I’m not sure exactly how to interpret that, but I suspect that Google wants this to get as little press as possible while the company scrambles to get as many Android devices updated as possible before the end of July. A source who cannot be identified, however, did say that Google fixed the vulnerability in February and sent the patch to its partners at the beginning of March.
 That’s a challenge, because many carriers have installed franken-versions of Android on devices sold two or three years ago with custom user interfaces and crapware pre-installed apps, and may not be able to turn out new, updated versions of their customized Android version quickly … or have a way to distribute them economically.
That’s a challenge, because many carriers have installed franken-versions of Android on devices sold two or three years ago with custom user interfaces and crapware pre-installed apps, and may not be able to turn out new, updated versions of their customized Android version quickly … or have a way to distribute them economically.
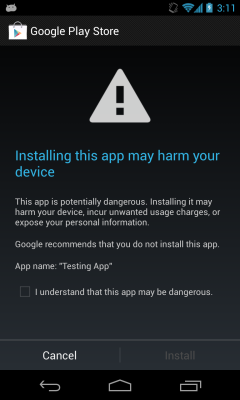
Users who are unsure of their phone’s update status or who are unable to update should be extremely cautious when installing apps, Bluebox says, and be sure to identify the publisher of the app before installing it. In addition, it’s a good idea to only install apps from Google Play, where Google has the ability to verify and validate apps.
VentureBeat has discovered that Google has added checks in Google Play which will guard against this type of attack, which means Google Play should be safe. An open question, however, is whether Google is offering the technology that can check for compromised apps to other, unauthorized Android app stores.
That’s important, because in some countries such as Korea, sources tell me that Google Play is not in wide use.
“In the U.S., Google Play is definitely dominant, but outside the U.S., Google Play is very small,” Hooked Media CEO Prita Uppal told me a little over a month ago.
That’s why getting the latest Android updates from a trusted source is critical.
“People should look to upgrade their Android devices and inquire with their device manufacturer to see if they are tackling this issue,” Forristal told me via email. “Enterprises need to invest in comprehensive mobile security solutions that protect the integrity of their data against these kind of vulnerabilities.”
I have learned that OEMs — phone manufacturers — and carrier partners were given the patch in March, basically as soon as Google had it for Google Play. But third-party Android app stores and their users are likely still at risk … as would be any user who installs Android apps they download privately or access from an email.
One thing you can do to ensure you are safe, regardless of which app store you frequent, is to use Google Play as an application verification tool regardless of where you’ve downloaded your apps. To do that, simply go to apps menu and tap Google Settings > Verify apps, or, in Android 4.2 and higher, go to Settings > Security > Verify apps.
For more information, check this Google resource.
VentureBeat's mission is to be a digital town square for technical decision-makers to gain knowledge about transformative enterprise technology and transact. Learn More