The latest revelations from NSA whistleblower Edward Snowden, who is currently seeking political asylum in Russia, hit the Internet today, and they’re staggering.
According to Snowden, the NSA has the capability to wiretap anyone, see real-time Internet browsing, monitor Facebook chat, and much more. Many of the revelations were backed up by a 2008 slide deck labeled “Top Secret” and only available to key individuals with high security clearances in the long-standing “five eyes” countries — USA, Australia, Canada, Great Britain, and New Zealand — which have long cooperated in matters of international intelligence.
Here is the document in its entirety:
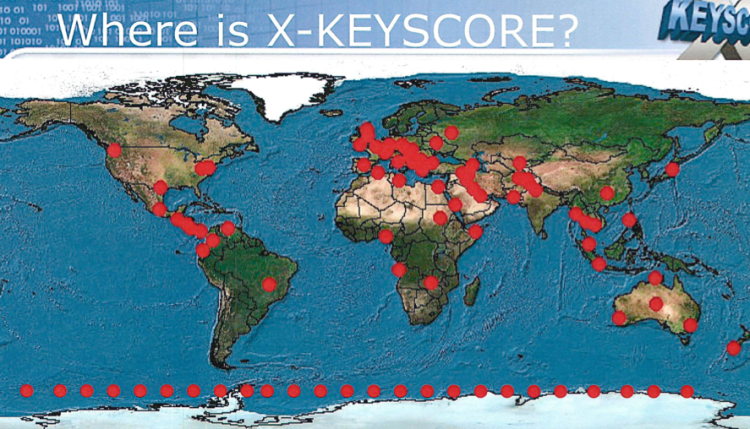
The document is clearly old, and sections are redacted. However, you can clearly see interesting and powerful capabilities in XKeyscore even from five years ago.
For example, the system used 150 sites all over the world in countries such as Egypt, Australia, India, Pakistan, Russia, and France to collect e-mail addresses, phone numbers, web chat logs, and sites visited, among other things. Even in 2008, the system had the capability to show intelligence analysts “all the encrypted word documents from Iran,” for instance, or all users of PGP (Pretty Good Privacy) in that country.
(Confirmed, once and for all: Use of encryption guarantees special interest from the digital men in black.)
In addition, the document seems to allege that the NSA had the capability to find all the Virtual Private Network startups (which would enable secure, private, encrypted communication) in a given country, and then decrypt the communications they were enabling.
“These events are easily browsable in XKeyscore,” the NSA document states.
XKeyscore also seems to have the capability to trace authorship and location of people who have written documents. The cited example is of “Jihadist document.” It could also show analysts “all the Microsoft Excel spreadsheets containing MAC addresses coming out of Iraq,” for instance. MAC addresses are unique identifiers for devices on digital networks.
Even more interesting, XKeyscore, according to this NSA document, maintained a database, called “Tao,” of “all exploitable machines in country X,” which seems to prove once and for all that American three-letter agencies do indeed possess strong capabilities for both finding vulnerable computers and then hacking or cracking them to aide in investigations.
As you would expect, the authors of this document say that XKeyscore is being updated with “new web services every day.” The question is, of course, what those web services are. Are they, for example, hooks into private companies’ databases or traffic logs?
XKeyscore has capabilities in English (of course) as well as Arabic and Chinese. I’m sure China is flattered that the U.S. considered China enough of a threat to include Chinese-language capabilities in a system ostensibly to protect against terrorists.
The document states that “over 300 terrorists” have been captured as a direct result of this system, which has captured over a trillion records and continues to add over 20 terabytes of data each and every day. In addition, the NSA’s rationalization for this type of surveillance seems to be, in part, that they don’t actually look at all the billions of pieces of data they collect.
“Both of these programs operate on a very large scale,” the NSA revealed. “However … only a tiny fraction of such records are ever viewed by N.S.A. intelligence analysts.”
One wonders, of course, if 300 million Americans’ freedoms have been imprisoned along with the 300 terrorists supposedly captured as a result of the program.
Not to say anything of billions of other global citizens whose private data is now in hundreds of NSA servers around the globe.