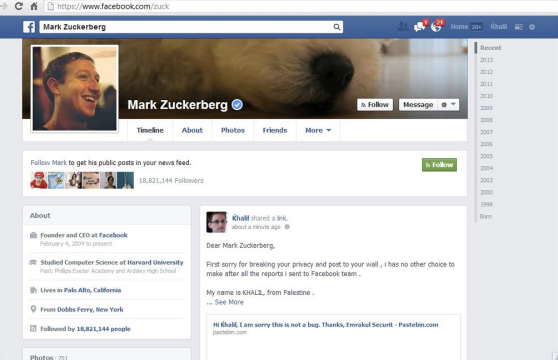
Khalil Shreateh, a Palestinian IT researcher, found a big Facebook security vulnerability, but Facebook ignored him. So he used the exploit to write on Mark Zuckerberg’s wall.
The hack violated a fundamental rule about how Facebook works: If you’re not friends with someone, you can’t write or post links on their walls. At least in theory.
While the vulnerability seems like a severe one, Shreateh says that Facebook didn’t take it seriously. After ignoring Shreateh’s messages twice, Facebook finally gave him a reply: “I am sorry this is not a bug,” the company said.
So, Shreateh says, he had no choice but to take the vulnerability all the way to top by posting a message directly on Facebook CEO Mark Zuckerberg’s personal Facebook page. This is what his message looked like:
That, as you might expect, really got Facebook’s attention. Within minutes, Shreateh got a reply from one of Facebook’s security engineers, who wanted more details about the vulnerability. (Facebook has since patched the vulnerability.)
But it’s what came afterwards that’s most interesting. Not only did Facebook temporarily disable Shreateh’s account, but the company also refused to pay him for discovering the vulnerability — all because of the way he went about reporting it.
“We are unfortunately not able to pay you for this vulnerability because your actions violated our Terms of Service. We do hope, however, that you continue to work with us to find vulnerabilities in the site,” the company told Shreateh in an email.
While it’s easy to dump on Facebook for its handling of the situation, considering Shreateh’s uneven use of the English language, it’s easy to see why it might have been tough to take him seriously. It also doesn’t help that Shreateh apparently didn’t provide enough information about the vulnerability in his initial report, which might have made it tough to follow-up.
Update: In a HackerNews thread, a Facebook employee gave some background about Facebook’s stance on the situation:
We get hundreds of reports every day. Many of our best reports come from people whose English isn’t great – though this can be challenging, it’s something we work with just fine and we have paid out over $1 million to hundreds of reporters. However, many of the reports we get are nonsense or misguided, and even those (if you enter a password then view-source, you can access the password! When you submit a password, it’s sent in the clear over HTTPS!) provide some modicum of reproduction instructions. We should have pushed back asking for more details here.
Still, Facebook should in good faith pay the guy. Considering that the company has paid hackers $1 million over the last two years for reporting bugs, something tells me it won’t miss a few extra bucks.
Here’s a video of the vulnerability in action.
http://www.youtube.com/watch?feature=player_embedded&v=F9J8U9ZpEnw