Mysterious “interceptor” cell towers in the USA are grabbing phone calls — but they’re not part of the phone networks. And, two experts told VentureBeat today, the towers don’t appear to be projects of the National Security Agency (NSA).
The towers were revealed by Les Goldsmith to Popular Science last week. He’s CEO of ESD America, which builds the super-secure Cryptophone 500 for clients that need the military-grade security and can handle the phone’s estimated $3,500 price tag.
In the course of testing the phone, Goldsmith’s team discovered the existence of phone cell towers that intercept a call and hand it off to the real network — allowing the tower to listen in or load spyware to the mobile device.
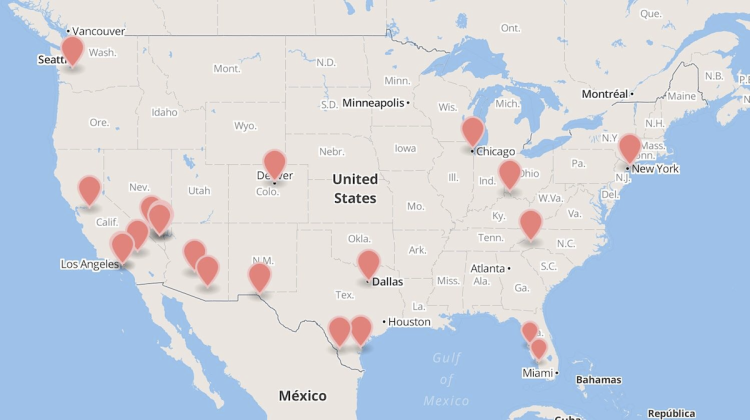
In July, ESD America identified 17 of the towers, but now it has increased that outed inventory to 19. On its Facebook page, ESD America points out that an interceptor “doesn’t necessarily need to be a[n] actual cell tower,” but could simply be the listening/call handling technology sitting somewhere.
Who is installing and managing these interceptors?
Not the NSA, cloud security firm SilverSky CTO/SVP Andrew Jaquith told us. “The NSA doesn’t need a fake tower,” he said. “They can just go to the carrier” to tap your line.
“I would agree with that,” Goldsmith told us. But then who?
They could be from perhaps law enforcement agencies or the military, he suggested. A number of these towers are around military bases, although they’re also found in other locations, including the vicinity of the South Point Casino in Las Vegas.
The discovery “appears to confirm real-world use of techniques that have been highlighted by researchers for years,” said Stephen Ellis, manager of cyber threat intelligence at security firm iSIGHT Partners. While noting that his company “cannot confirm the accuracy of this reporting without further information,” Ellis told us that iSIGHT is “highly confident that we have observed real-world use of this technique in support of another of its uses – cyber crime [for] financial gain.”
“We have observed and reported on cases in other parts of the world where actors are known to have set up fake base stations to send spoofed SMS messages,” Ellis said, “possibly to send spam or to direct unsuspecting victims to malicious websites.”
The Federal Communications Commission (FCC) announced last month that it is launching an investigation into the use of cell network interceptors by criminal gangs and foreign intelligence.
We asked Goldsmith if he could be mistaken about the towers. Perhaps they are just commercial ones that seem unusual?
“We can definitely tell” that they’re non-network towers, he said, by analysis of the infrastructure. These phony towers, without names as normal towers have, insist to your phone that they must handle the call and then trick the phone into turning off its normal encryption.
Such a tower tells you that “none of your towers are currently available,” Goldsmith told us. It says, “‘I’m your tower.’
“If you wanted to listen to a phone call,” he said, “this would be the easy way.”