Cybersecurity made it onto the list of the top five concerns of U.S. electric utilities this year, according to a new Black & Veatch survey. And less than a third of respondents said they’re equipped to handle an attack.
And it’s not just energy companies that are worried. Boards of hundreds of U.S.-based corporations are realizing they’re unprepared for the growing threats of cyber attacks as well.
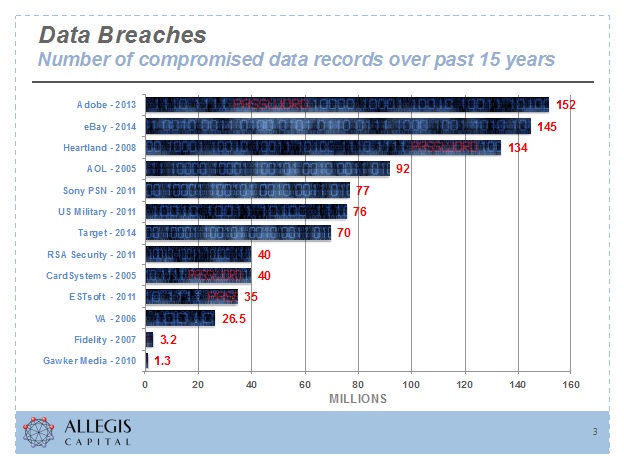
Long viewed primarily as just a “technology” problem, cyber security is rapidly moving up the list of critical business and governance concerns in corporate boardrooms. And that makes sense given the list of companies that have faced serious breaches over the last few years.
Cyber security is a matter of enterprise risk. Think about it: What if your research results were stolen? Your supply chain compromised? Your ability to conduct business on a day-to-day basis shut down? Your strategy for business negotiations compromised?
Boards must develop the expertise to bring adequate governance to overseeing their company’s cyber infrastructure. Boards need to add members who are conversant in the inherent risks of a digital infrastructure and can engage operational management from a position of knowledge and experience. Cybersecurity cannot be treated as a “tick the box.” Get it wrong and the company could be out of business.
So what does the board and C-suite need to do? Get started on developing a cyber healthcheck.
Here are four strategies to consider.
1. Develop a crisis cyber plan. Corporations will be breached, and they need to know how they will respond when “bad guys” compromise them. Boards must have an action plan in place — executable at a moment’s notice. When reviewing business processes to support commercial enterprise initiatives, the risks associated with enabling IT infrastructure must be an essential part of the discussion. What can go wrong? How would it go wrong? What are the consequences if (and when) we are compromised? What can we do to lower the potential damage when we are breached? Cybersecurity must become part of the screening process for all business activity. In anticipation of attacks, the company should develop a plan to identify potential attackers at a distance and make it harder for them to successfully attack (raise the cost to the attackers), while also facilitating containment and rapid remediation when a breach takes place.
2. Determine ownership of the “enterprise risk.” Key executives (CEO, general counsel, chief financial officer, chief information officer (CIO), and chief information security officer (CISO)) must all be involved in identifying cyber risks and developing and implementing an effective strategy for managing the consequences of a successful breach. Are we entering the era of the Chief Risk Officer? It is essential to have a multidiscipline perspective that can provide the board with information about the variety of cross-function cyber risk issues, including identifying the vulnerabilities that are inherent in the gaps associated with integrated systems. Too often today the audit committee is assigned responsibility for cyber. It’s a rational place to start, but the strategy has to come from management with broad board understanding, review, and oversight. Cyber is “100% — all the time.” It can’t be left to the auditors.
3. Review the company’s cybersecurity insurance. Unfortunately, most organizations are uninsured and those that have coverage are oftentimes under-insured. The complexities of cybersecurity and the limited ability to adequately define costs and consequences, ensures that the risks associated with a successful breach cannot be fully insured against. At the same, insurance can provide the resources to mitigate some of the risk when a breach occurs. In searching for insurance, you should anticipate that insurers will require some form of “cyber health check.”
4. Understand the standards and regulations. Today, calls for more reporting, disclosure, and transparency around cyber security preparedness and successful breaches are growing louder. Get on top of the challenge; don’t wait for it to become a crisis. Here are some resources that may help:
- ISO/IEC 27032 An international standard that contains baseline security practices for companies.
- The National Institute of Standards and Technology (NIST) Cyber security Framework: A framework of best practices based on a variety of international cybersecurity standards that companies can use to assess their own cybersecurity maturity.
- The SANS Institute Critical Security Controls
These guidelines feature a list of 20 prioritized security controls that have been deemed to be effective to combat cyber attackers by a group of public and private security experts.
An enterprise’s cyber security posture is essential to viably and profitably do business today. Cybersecurity today may well represent the greatest external (and sometimes internal) threat to an enterprise’s viability. It’s the responsibility of the board of directors to ensure that their company is up to the challenge.
Bob Ackerman Jr. is the founder and a managing director of Allegis Capital, an early stage Silicon Valley venture capital firm that invests heavily in cyber security.
VentureBeat's mission is to be a digital town square for technical decision-makers to gain knowledge about transformative enterprise technology and transact. Learn More