Want smarter insights in your inbox? Sign up for our weekly newsletters to get only what matters to enterprise AI, data, and security leaders. Subscribe Now
Online betting giant Betfair has been compromising security by letting people change their passwords with nothing more than a valid date-of-birth (D.O.B) and email address — and no email verification is required to make the change.
That means it would be all too easy for someone else to change your password and take over your account.
This security gap has now been closed, and there’s no evidence that any Betfair accounts were compromised. But it’s not clear how long this flaw was open or how many users it could have affected, and Betfair’s response to inquiries from VentureBeat and others suggest that the company may not have fully understood the nature of the risk.
Founded in the U.K. in 1999, Betfair has grown to become one of the largest betting exchanges in the world, recording revenues of almost $600 million a year from 1 million customers. The company also trades on the London Stock Exchange.
AI Scaling Hits Its Limits
Power caps, rising token costs, and inference delays are reshaping enterprise AI. Join our exclusive salon to discover how top teams are:
- Turning energy into a strategic advantage
- Architecting efficient inference for real throughput gains
- Unlocking competitive ROI with sustainable AI systems
Secure your spot to stay ahead: https://bit.ly/4mwGngO
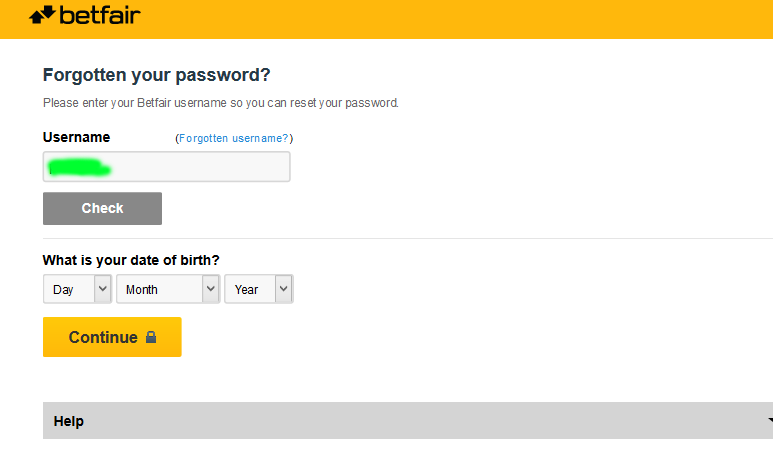
Password recovery
As with most online account-based companies, Betfair offers a password recovery tool for forgetful people. With Betfair’s tool, however, some users were — until yesterday — asked to enter their username or email address, then they were invited to input their D.O.B.
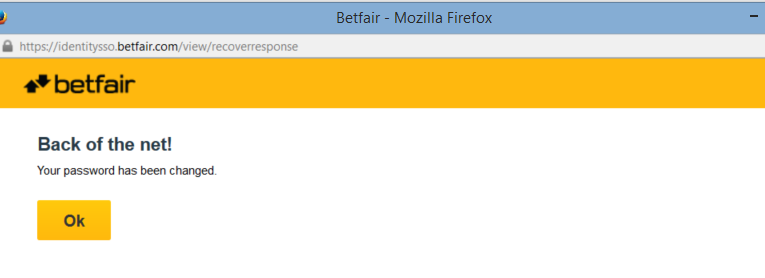
Users could then freely choose a new password, and continue on to their account without any further obstacles such as email verifications.
Once in the account, users were able to operate as normal, including viewing and editing personal details, placing bets, and, importantly, changing the email address.
While Betfair did issue an automated email notifying the real account holder of the password change, this wasn’t part of any verification process. In the email it says:
“If it wasn’t you who made the change, you’ll need to get in touch with the Helpdesk ASAP via one of the contact us options.”
“Feature” not flaw
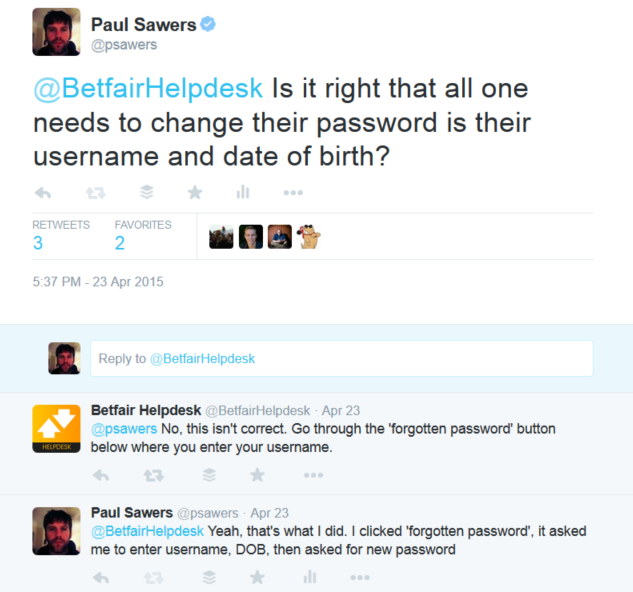
I first got wind of this security flaw last week while recovering a long-forgotten password. So like any self-respecting Internet-dweller, I took to Twitter to ask Betfair’s customer service team whether what I’d just experienced was correct, or whether I was suffering early-stage senility.
It turns out that Betfair said I was mistaken, which led us down a long path of discussion that got increasingly more painful. You can read the full chat here if you like, but the gist of it is that there was a lot of repeated questions, frustrating answers, and head banging against desks.
In the end, Betfair finally conceded that all someone needed is a username/email address and date-of-birth to change a password. But it still maintained that for the accounts it was testing in-house, there was no such issue. So basically it seemed like it didn’t know what the full situation was.
VentureBeat contacted Betfair’s communication department on April 23, and after a little persistence received a response yesterday (April 28). As of yesterday morning, the security flaw was still active, but at some point during the day the issue was fixed. The first email response from Betfair was this:
“The procedure you have identified is correct for some accounts, although there is a threshold above which additional verification is required.
We take security extremely seriously and were the first to enable a two-step authentication process where all customers can add an additional pin code to access accounts in addition to their password. We also operate a closed loop system where funds can only be returned to the payment card that they have come from.
Having said this, we are aware of the issues you raise. We constantly review our procedures and are doing so in this case.”
After further probing regarding the “some accounts” element of its explanation, Betfair elaborated and said it had launched a “recent trial for a small number of accounts.” So in effect, Betfair says this is a test it was deliberately doing, not an undetected flaw.
It’s not quite clear at this stage what advantage there is to removing email verification from the security process, given that it only takes 10 seconds to click on a link contained within an email. Betfair has also refused to comment further on their reasons for introducing this feature, or the scale of its rollout.
However, looking across the web to see if anyone else had encountered this, I found a handful of forum posts such as this one dating back to September, while a London-based Yahoo developer had reported the issue in December via Twitter.
@troyhunt interesting – if you have <£100 in your BetFair account you can change password with just username and DOB! pic.twitter.com/bd1TRafR86
— Tom Thorpe (@thorpetom) December 28, 2014
Also, following my Twitter conversation with Betfair, a number of people tested it out themselves to see if they could replicate the issue, and everyone I encountered could.
Troy Hunt, an Australia-based software architect and Microsoft MVP Award holder for developer security, was one such person who picked up the baton. He set up a Betfair account and was able to change the password with just his email address and date-of-birth. He even created this handy walk-through video showing the feature in action.
Hunt also contacted Betfair’s customer support team in Australia, and in a blog post about his experience, he reported:
“The call finished with my request to delete the account and remove all my data. She called back a little later confirming the account had gone and that also, yes, I (and of course Paul) were correct in terms of the password reset behaviour. She explained that it’s the UK’s fault (seriously) in that the software product had come from there.”
So the upshot of all this is that there have been confusing messages: The original response from Betfair’s customer support team on Twitter stated that I was mistaken, but later it said it did have such a system in place “years ago,” but not any more. It finally conceded that the system was still in place.
Betfair’s main communications department also confirmed to VentureBeat that it was aware of the issue, but implied it wasn’t a flaw … it was a feature. And according to Hunt, Betfair made it sound like it could be a software issue, though VentureBeat hasn’t been able to verify this independently with Betfair.
As of now, Betfair isn’t answering any follow-up questions to clarify the situation beyond a “no comment.” However, earlier today a further security flaw was identified by a Reddit user.
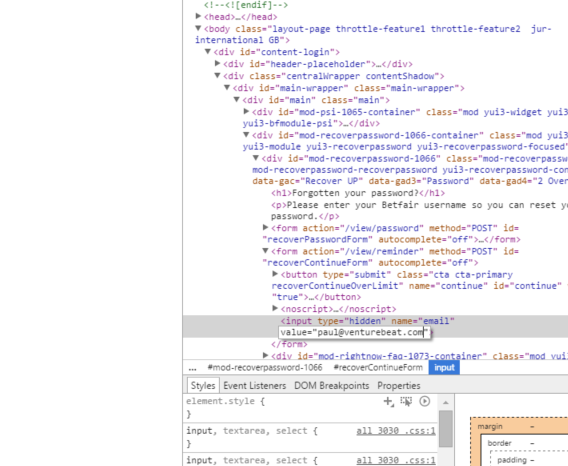
Hidden input field
There was a hidden input field for the email address buried in the HTML code, which was accessible through the password recovery tool section of Betfair. Using a browser’s built-in developer tools to inspect the elements of a web page, a feature that’s often used to debug websites, anyone could edit the email address where the password recovery was to be sent.
For example, in the password recovery section of Betfair, all anyone needed to do was enter a valid username or email address into the “Username box,” then right-click on the “Send Reminder” button, edit the email address within the HTML code that pops up, and then send it. VentureBeat tried this out, and it did indeed work.
U.K.-based programmer and self-proclaimed “IT geek” James Harland has created a screencast of this process in action.
VentureBeat can now confirm that this security hole has also been closed off as of today, though Betfair doesn’t say how long this was in place for. It did release this statement though, specifically for the latest lapse:
“A flaw was discovered in our password recovery flow this morning. Our development teams have now fixed the flaw, and our security teams have tested it successfully. We are reviewing the situation and impact, and we are currently carrying out a full security review of our process to ensure that there are no more vulnerabilities.”
Bigger picture: “Logical and technical flaws”
In the grand scheme of things, how bad were these security lapses? Well, the good news is that it seems nobody has been directly impacted by this. We’ve not seen any reports of anyone’s account being accessed illegitimately using the methods highlighted above. But that’s perhaps down to fortune more than anything else.
In an interview with VentureBeat, security expert and blogger Graham Cluley said it was “gobsmacking” that such a security lapse had been permitted, especially by a company of Betfair’s size and position.
“Online betting companies should be taking security as seriously as online banks,” he says. “You should have 2-factor authentication like Fort Knox to make sure only the right people get in. This is jaw-dropping incompetence.”
Certainly, the initial issue identified last week has clearly been known about for a while, but it was only after VentureBeat contacted Betfair that the company changed it. There can’t be any justification for allowing a password-change using information that’s freely available — anyone with a Facebook account will likely disclose their email address and date-of-birth to hundreds or thousands of people.
“I’ve seen a lot of bad practices in other areas of Internet software but this would certainly rate as one of the worst I’ve seen,” says security expert Troy Hunt. “The password reset using easily discoverable data attributes, such as email and birth date, is a serious logic flaw. The subsequent one identified today, involving sending a reset link to an arbitrary email address, is a flaw in the technical implementation. That we see both logical and technical flaws in the one app is very worrying.”
Whether any damage was ultimately done or not is almost irrelevant. It all boils down to how a user’s personal details are treated — it shouldn’t matter whether it’s a free knitting forum or multi-national betting company. The damage that could be done with the latter, however, could be far more serious.
Show me the money
While it was possible to change just about every detail within a Betfair account after accessing it using the methods outlined here, you’re probably also wondering whether it would’ve been possible to remove funds from the account. Betfair says it would NOT have been possible: “We operate a closed loop system where funds can only be returned to the payment card that they have come from.”
That doesn’t tell the full story, however. Before closing my account I managed to withdraw the remaining funds to my PayPal account, which hadn’t been registered with Betfair up until the point of withdrawal. This means anyone who had gained access to my Betfair account could potentially have withdrawn it to their own PayPal account.
However, Betfair says there is a strict process in place to minimize the chances of fraud. A spokesperson told VentureBeat:
“PayPal can be used to withdraw but it is strictly monitored by our fraud, payments, and anti-money-laundering teams, who have a series of checks to link PayPal accounts to the Betfair account holder.”
So, because the owner of the PayPal account (me) was the genuine owner of the Betfair account, this could explain why I was able to withdraw the funds without any issues. But without any further elaboration from Betfair on their exact processes here, it’s difficult to know for sure.
It can be easy to get desensitized to security lapses when there are so many prominent examples in the headlines. But when things go wrong, it can have serious consequences for everyone involved, beyond that of bad publicity — just ask Target, and just ask Home Depot.
Any company that holds sensitive and private information on its customers — not to mention their cash — has to treat security with the utmost respect at all times. Here’s hoping Betfair can learn from this. Otherwise, more people may soon start closing their Betfair accounts.