After releasing Chrome 40 for iOS just yesterday, Google today launched Chrome 40 for Windows, Mac, Linux, and Android. You can update to the latest desktop release now using the browser’s built-in silent updater or download it directly from google.com/chrome, and grab the Android release from Google Play.
The Android version should go first, as there’s not as much to say — this isn’t a big release for Google’s mobile operating system, unlike on iOS. The new version brings improvements for Android 5.0 Lollipop, faster network performance, and the usual slew of bug fixes. That’s it — no groundbreaking additions.
The biggest change in the desktop release is the blocking of Netscape Plugin Application Programming Interface (NPAPI) plugins in Chrome by default, as promised. Google hopes this will improve the browser’s security, speed, and stability, as well as reduce complexity in the code base.
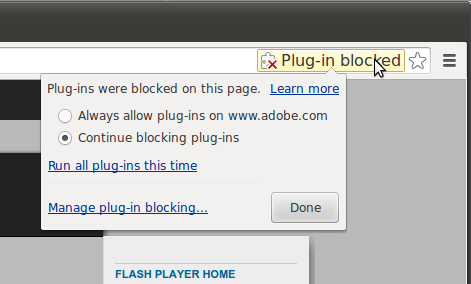
Google first announced in September 2013 that it was planning to drop NPAPI, though delays (adoption was still relatively high for many months) pushed back its plans until this year. In Chrome 40, users can still allow NPAPI plugins for specific sites by clicking on the “Plug-in blocked” message in the URL bar and choosing “Always allow plug-ins on [website].” Here is how that looks:
There are two more steps left on Google’s roadmap to kill NPAPI. In April 2015, the above workaround will no longer exist, as NPAPI support will be disabled by default in Chrome and Google will unpublish extensions requiring NPAPI plugins from the Chrome Web Store. That said, Google will provide an override for advanced users (via an “enable-npapi” flag) and enterprises (via Enterprise Policy) to temporarily re-enable NPAPI.
In September 2015, Google will scrap the workarounds and permanently remove NPAPI support from Chrome. NPAPI plugins will simply no longer load, regardless of whether they are needed by websites or extensions. Web developers who use or build these plugins can find out more information in the NPAPI deprecation guide.
Next up, Chrome 40 also scraps version 3.0 of the SSL protocol, removing a serious security vulnerability the company revealed on October 14. This is the last in the company’s plan to address the issue in its browser, protecting Chrome users from services and websites that can still try to exploit the flaw.
Speaking of protection, Chrome 40 also includes 62 security fixes, of which Google chose to highlight the following:
- [$5000][430353] High CVE-2014-7923: Memory corruption in ICU. Credit to yangdingning.
- [$4500][435880] High CVE-2014-7924: Use-after-free in IndexedDB. Credit to Collin Payne.
- [$4000][434136] High CVE-2014-7925: Use-after-free in WebAudio. Credit to mark.buer.
- [$4000][422824] High CVE-2014-7926: Memory corruption in ICU. Credit to yangdingning.
- [$3500][444695] High CVE-2014-7927: Memory corruption in V8. Credit to Christian Holler.
- [$3500][435073] High CVE-2014-7928: Memory corruption in V8. Credit to Christian Holler.
- [$3000][442806] High CVE-2014-7930: Use-after-free in DOM. Credit to cloudfuzzer.
- [$3000][442710] High CVE-2014-7931: Memory corruption in V8. Credit to cloudfuzzer.
- [$2000][443115] High CVE-2014-7929: Use-after-free in DOM. Credit to cloudfuzzer.
- [$2000][429666] High CVE-2014-7932: Use-after-free in DOM. Credit to Atte Kettunen of OUSPG.
- [$2000][427266] High CVE-2014-7933: Use-after-free in FFmpeg. Credit to aohelin.
- [$2000][427249] High CVE-2014-7934: Use-after-free in DOM. Credit to cloudfuzzer.
- [$2000][402957] High CVE-2014-7935: Use-after-free in Speech. Credit to Khalil Zhani.
- [$1500][428561] High CVE-2014-7936: Use-after-free in Views. Credit to Christoph Diehl.
- [$1500][419060] High CVE-2014-7937: Use-after-free in FFmpeg. Credit to Atte Kettunen of OUSPG.
- [$1000][416323] High CVE-2014-7938: Memory corruption in Fonts. Credit to Credit to Atte Kettunen of OUSPG.
- [$1000][399951] High CVE-2014-7939: Same-origin-bypass in V8. Credit to Takeshi Terada.
- [$1000][433866] Medium CVE-2014-7940: Uninitialized-value in ICU. Credit to miaubiz.
- [$1000][428557] Medium CVE-2014-7941: Out-of-bounds read in UI. Credit to Atte Kettunen of OUSPG and Christoph Diehl.
- [$1000][426762] Medium CVE-2014-7942: Uninitialized-value in Fonts. Credit to miaubiz.
- [$1000][422492] Medium CVE-2014-7943: Out-of-bounds read in Skia. Credit to Atte Kettunen of OUSPG.
- [$1000][418881] Medium CVE-2014-7944: Out-of-bounds read in PDFium. Credit to cloudfuzzer.
- [$1000][414310] Medium CVE-2014-7945: Out-of-bounds read in PDFium. Credit to cloudfuzzer.
- [$1000][414109] Medium CVE-2014-7946: Out-of-bounds read in Fonts. Credit to miaubiz.
- [$500][430566] Medium CVE-2014-7947: Out-of-bounds read in PDFium. Credit to fuzztercluck.
- [$500][414026] Medium CVE-2014-7948: Caching error in AppCache. Credit to jiayaoqijia.
- [449894] CVE-201X-XXXX: Various fixes from internal audits, fuzzing and other initiatives.
- Multiple vulnerabilities in V8 fixed at the tip of the 3.30 branch (currently 3.30.33.15).
Google also rewarded Atte Kettunen, Christian Holler, cloudfuzzer, and Khalil Zhani with $35,000 for preventing security bugs from ever reaching the stable channel. If you add all those up, you’ll see Google spent a whopping $88,500 (more than double the last version) in bug bounties for this release.
The security improvements alone should be enough to push the hundreds of millions of Chrome users to upgrade to version 40.
VentureBeat's mission is to be a digital town square for technical decision-makers to gain knowledge about transformative enterprise technology and transact. Learn More