GitHub today announced it has fixed 57 previously unknown security vulnerabilities in its applications thanks to its bug bounty program, which launched just a year ago. Given this success, the company is now doubling the maximum bounty payout from $5,000 to $10,000.
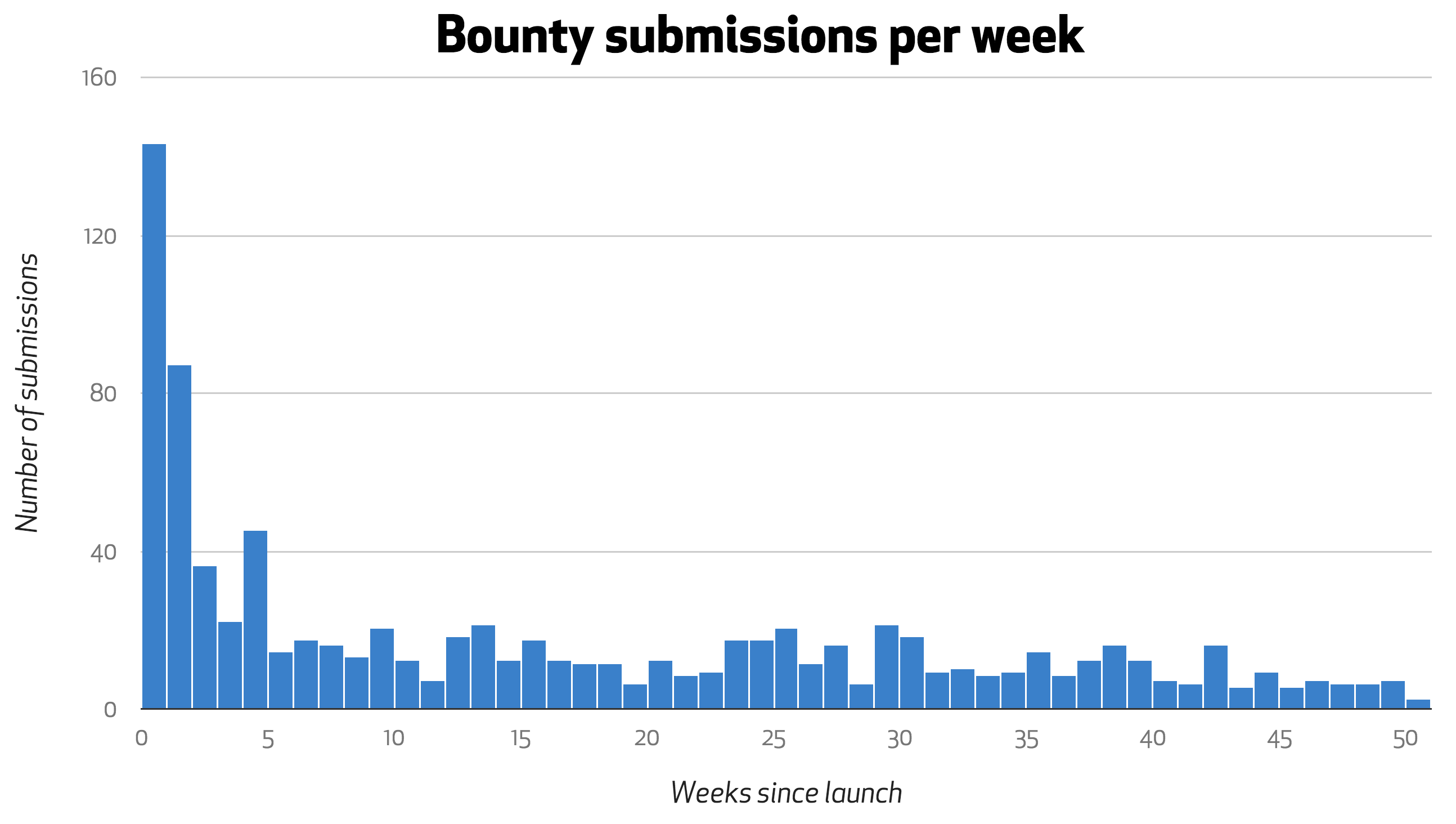
The number of bugs was significantly smaller than the 1,920 submissions GitHub received in the past year. The company first cut down that number to 869 reports that actually “warranted further review.” Here is the breakdown of the submissions on a weekly basis:
Just like when it launched, GitHub’s bug bounty program covers the GitHub API, GitHub Gist, and GitHub.com. The company’s other Web properties and applications are not part of the program, but vulnerabilities found “may receive a cash reward at our discretion.”
AI Weekly
The must-read newsletter for AI and Big Data industry written by Khari Johnson, Kyle Wiggers, and Seth Colaner.
Included with VentureBeat Insider and VentureBeat VIP memberships.
The exact amount paid out for each bounty is determined by GitHub based on the actual risk and potential impact to users. That means the bigger the potential scope and the greater the severity of the issue, the larger the payout.
GitHub today detailed some of the more interesting security vulnerabilities that were discovered:
Our top submitter, @adob, reported a persistent DOM based cross-site scripting vulnerability, relying on a previously unknown Chrome browser bug that allowed our Content Security Policy to be bypassed.
Our second most prolific submitter, @joernchen, reported a complex vulnerability in the communication between two of our backend services that could allow an attacker to set arbitrary environment variables. He followed that up by finding a way to achieve arbitrary remote command execution by setting the right environment variables.
Bug bounty programs are used by much larger tech companies, including Facebook, Google, and Microsoft with great results. While GitHub may not have their size and scope, its program is still clearly worth the hassle: It’s always better to find and fix a bug before it becomes a problem, especially when it comes to security. Rewarding security researchers with bounties costs peanuts compared to the cost of paying for a security disaster.
Unfortunately, GitHub didn’t share how much it paid out in total for 2014, nor to how many security researchers. We contacted the company about these tidbits and will update you if we hear back.
Update: 33 unique researchers earned a cumulative $50,100 for the 57 medium to high risk vulnerabilities they reported, GitHub told VentureBeat.
VentureBeat's mission is to be a digital town square for technical decision-makers to gain knowledge about transformative enterprise technology and transact. Learn More