Nintendo fans with Android phones, beware. A new piece of Android malware is showing up in third-party app stores dressed as a classic Nintendo game.
Cybersecurity firm Palo Alto Networks says it has discovered a new family of malware that looks and behaves like advertising software, all while stealing personal information from infected Android devices. The malware is called Gunpoder, and it’s hidden in a gaming app.
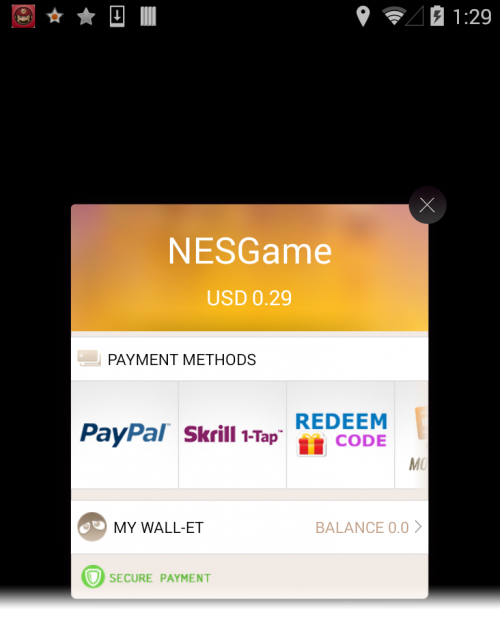
The app is based on an open-source Nintendo Entertainment System emulator (an app that runs classic Nintendo games from the 1980s and early 1990s on mobile) and is available in third-party app stores. The bad actors behind the Gunpoder malware took the original emulator and added a payment function, advertising software, and a text feature that promotes the game using a device’s contact list. The result is a paid app that also steals your personal information.
Here’s how it works: Once downloaded, the app serves users a message that says the emulator is ad-supported. By touching “OK,” you are agreeing to let a program called Airpush collect data from your device. Airpush is a library typically used to push in app mobile ads. Within this NES emulator, however, it collects lots of personal information from a device, including a user’s location, their contact list, bookmarked websites, as well as information about the device itself.
“They’re trying to build a profile of people so they can target them for spearfishing or other malicious activity in the future,” says Scott Simkin, the senior threat intelligence manager at Palo Alto Networks. In addition to being able to target users for future attacks, Simkin says hackers can also sell user information on various webforums.
After users agree to have their data collected, the app serves up another notice asking users to purchase a “lifelong license.” If users agree, the app collects their payment information and charges them $0.45 for the license.
Palo Alto Networks says that using Airpush allows Gunpoder to avoid detection by antivirus software. Most antivirus software doesn’t block or detect adware as malware.
When the cybersecurity firm submitted several types of the Gunpoder virus to VirusTotal, a free platform for determining whether a file has been infected, they all showed up as either “benign” or “adware,” according to a report.
“Legacy controls would not prevent installation of this malware. While researching the sample, we observed that while it contained many characteristics of adware, and indeed embeds a popular adware library within it, a number of overtly malicious activities were also discovered, which we believe characterizes this family as being malware,” the report said.
In addition to being undetectable by antivirus software, the malware is also spreading. Users of the purported NES game are asked to share the app with their contacts via SMS, thus infecting a whole new crop of Android devices.
Palo Alto Networks says it found 49 unique samples of the malware that have potentially been deployed in a slew of countries including the United States, Iraq, Thailand, India, Indonesia, South Africa, Russia, France, Mexico, Brazil, Saudi Arabia, Italy, and Spain.
Simkin claims customers of Palo Alto Networks enterprise security software are now safe from this kind of malware. However, general consumers are not. In order to avoid Gunpoder, users should avoid downloading apps from third-party sites. “The second you step out of their approved app stores, you can completely trick the user,” says Simkin.
This is the second instance of malware based on open-source code that Palo Alto Networks has found, and it expects this trend will only grow. As Simkin says, “The more an attack is successful, the more attackers are going to share information about it.”
VentureBeat's mission is to be a digital town square for technical decision-makers to gain knowledge about transformative enterprise technology and transact. Learn More