Just when one (tech) media firestorm over Uber’s privacy policies starts to subside, another story emerges about the surprising amount of user data collected by the company’s mobile app for Android.
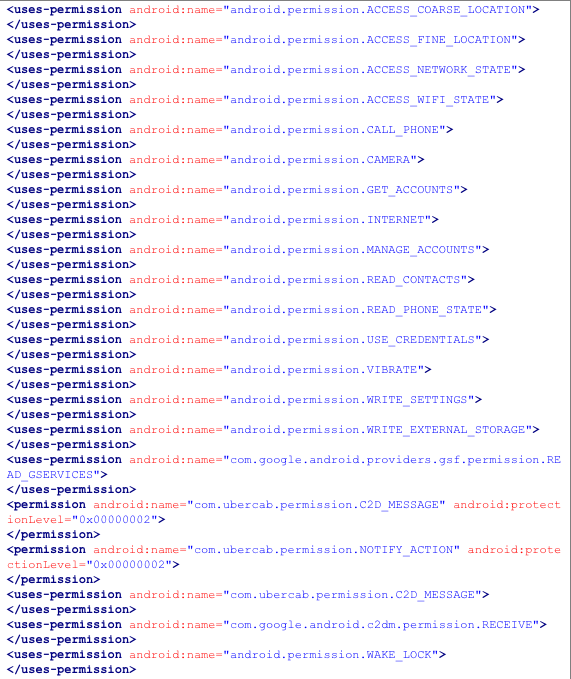
A security researcher in Arizona described in a blog post Tuesday how he decompiled the app’s code, and uncovered a lengthy list of data requests made by the app.
The researcher, Joe Giron, wrote that some of the data collected seems strange and unnecessary. For instance, the app asks for information about the user’s neighbor’s Wi-Fi service, whether or not your phone is jailbroken, and whether or not the phone might be vulnerable to the Heartbleed bug.
“Christ man! Why the hell would it want access to my camera, my phone calls, my wifi neighbors, my accounts, etc?” Giron says in the blog.
The app accesses voice call and messaging histories, data usage history, Wi-Fi connections, and any kind of Device ID that may be available. Device ID is often used to target ads at specific devices.
The Uber app also asks for information about the other apps running on the user’s mobile device. It wants to know the identities of the apps, when they were installed, if they came as part of a bundle, how much data they use, and other stats.
Many of the data points collected by the app might be used for completely legitimate and useful purposes. Collecting the network connection information (like Wi-Fi) seems justifiable, as does the collection of the GPS data. The app also asks to use the camera so that users can add a picture to their profile.
“Access to permissions including Wifi networks and camera are included so that users can experience full functionality of the Uber app,” Uber said in an email response to VentureBeat.
“This is not unique to Uber, and downloading the Uber app is of course optional.” Uber also pointed us here for an explanation of the app’s various data requests.
But the information about the HeartBleed bug and whether or not the phone has been jailbroken seems unjustifiable, unless Uber plans to exploit that weakness in some way, which isn’t likely.
An Uber spokesperson explains that the code in the app that requests that information from the phone wasn’t put there by Uber.
“Our code lists several features that our mobile security vendor offers, but that we do not use,” the company says in a statement. “For example, ‘whether device is rooted, whether it has any malware on it, and whether it’s vulnerable to the Heartbleed security bug’ are not features that Uber uses.”
Like all Android apps, the Uber app displays a permissions page after downloading that the user must consent to.
But the extent of the data the Uber app collects seems to go beyond the data set shown on the permissions screen.
Giron notes that all the data points the app wants to access are listed in the “AndroidManifest.xml” file inside the Android application development kit (APK).
Here’s a screen grab of that file:
Of course this all comes just a week after Uber got into some hot water by threatening to track the movements of a journalist who had been critical to the company.
A media study conducted at the end of last week showed that many people were less concerned about the privacy of a single journalist and more concerned about the implication that Uber might not protect the privacy of users.
So the appearance this week of Giron’s research into the data collected by the Uber app may have struck a raw nerve.
VentureBeat's mission is to be a digital town square for technical decision-makers to gain knowledge about transformative enterprise technology and transact. Learn More