We all know cyber security is a hot issue these days. A new hack or cyber security threat seems to make headlines each week. The most recent news on this front, of course, is that hackers have accessed 50 million user accounts of Avid Life Media, the owner of cheating service Ashley Madison and dating sites Established Men and Cougar Life. These hacks are of course costly, and having your Ashley Madison account exposed could upend your personal life, but they’re not just about economics and embarrassing people, they are, without exaggeration, about terrorism, 21st century warfare and the safety of you and your family.
If we assume that half of the 50 million compromised Avid Life records are U.S. records, which seems a conservative assumption, and that the people who used the sites are representative of the general population, then the numbers below represent roughly the number of Americans in each of those categories.
- 1,250 Federal and State elected officials
- 2,500 FBI employees
- 2,500 NSA employees
- 2,175 full time nuclear power plant workers
- 3,500 TSA employees
- 25,000 DHS employees
- 35,000 local elected officials
- 60,000 people with top secret security clearance
These are people whose marital indiscretions, nude pictures, and sexual proclivities are now in the hands of anonymous hackers calling themselves the Impact Group. If that doesn’t scare the hell out of you, then you have clearly never seen a good spy movie.
[Note: I haven’t taken into account here the percentage of accounts that might be duplicates (one person might have accounts on more than one of Avid’s services). The numbers are intended simply to illustrate how big the potential problem is, not to be taken as concrete.]
Cyber security has two fronts, the first is the technological front where we need to respond directly to hackers, the second is the human front where hackers use social engineering to convince others to hand over access to their systems. The Ashley Madison data is like a WMD on the social engineering front. Why bother trying a brute force hack of a nuclear power plant’s control systems when you can threaten to destroy the plant’s IT director’s family, reputation, and career. I suspect there is a rather large team at the NSA working to identify everyone with security clearance placed at risk by the Ashley Madison breach. At least I hope there is. The problem is, what do you do when the list is so large? I don’t know if there is a solution other than leaking the entire list of names to the public, effectively firing the hacker’s bullets before they have a chance to do harm.
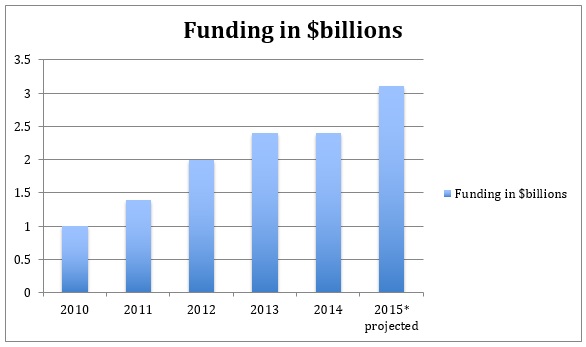
The venture and startup community has certainly recognized part of the danger here and has responded accordingly. Funding for security in 2010 was just over one billion dollars but has been growing steadily and is on pace to exceed three billion in 2015.
Here is a chart from Mattermark showing growth in security funding over the last five years.
As the funding data demonstrates, the current answer to cyber security is accelerating investment in technological solutions. This increased investment in cyber security is absolutely the right thing to be doing, but it can’t be the entire strategy for dealing with cyber crime for a couple of reasons. First, reactive technology development is too slow to stop a potentially devastating attack, and second, cyber security investment largely deals with only the first front in cyber security, leaving the human weakness exposed.
Defensive measures always lag offense and are never perfect. Swords entered use around 3,300BC, and mail armor rendering those swords less effective appeared in 400BC. The gun was introduced to Europeans in the 16th century, but a commercially available bullet-proof vest didn’t exist until the 19th century. The Nazis introduced modern missile technology in the early 1940s, but it wasn’t until the 2000s that a credible (barely) missile defense system existed. Defensive technology is by definition a response to an offensive technology of some sort and often only comes along as a direct response to an attack.
The pace of technology development has increased, and the lag time between offensive weaponry and defensive innovation is shrinking, but at the same time the damage a potential zero day attack can cause has been increasing at an even greater rate. No matter how much money is poured into cyber security, there will always be a gap between new attacks and our ability to respond to them. As cyber attacks become more sophisticated and our world becomes more connected, we are approaching a point where we can’t afford the damage a single attack can cause before we mount a defense.
The bigger issue, though, is that people ultimately control our systems, and people are weak. As long as any porn site, search history, social network, or job seeking site is vulnerable to being hacked, the people who use those sites and every system they have access to are vulnerable. The human weakness basically means that we are only as secure as the least secure site.
Recently, in response to the online privacy discussion, there has been a small but growing minority calling for openness and a post-embarrassment world. This burgeoning movement towards radical transparency is largely motivated by progressive sex-positive attitudes and a pragmatic understanding of how the Internet works. While I think both are reasonable bases for pushing for a more transparent world with less shame, the more compelling reason to “let it all hang out” is national security. If everyone’s porn preferences were known today, would anyone care six months from now? We have a cultural weakness exposed by modern technology and only a cultural solution can fix it. Is embracing a blasé attitude towards the personal lives of others something we can do overnight? Of course not, but plenty of other western nations, particularly France, have a much more open mind about the sorts of things that here in the U.S. are fodder for blackmail.
If we want to craft a credible defense against cyber terrorism, we need to attack it from all fronts. We need to continue investing in counter measures, but we also need to recognize that 20th century concepts of personal privacy place us all at risk in a 21st century world. Shame might be the strongest weapon our nation’s enemies can wield against us.
Jake Chapman is a partner at Sazze Partners, where he invests in founders making the impossible possible through sheer force of will. You can reach Jake at https://twitter.com/runvc.
VentureBeat's mission is to be a digital town square for technical decision-makers to gain knowledge about transformative enterprise technology and transact. Learn More