This post has not been edited by the GamesBeat staff. Opinions by GamesBeat community writers do not necessarily reflect those of the staff.
We live in trying times. As Sony discovered last spring, the security of customer information has become a matter of grave trust. Unfortunately, when hackers are determined and sufficiently motivated, no system is entirely secure. In the case of the PlayStation Network hack, that attack was motivated by ideological opposition to business decisions made by the Sony corporation. It was unfortunate that Sony’s customers found themselves in the crossfire, but the outcome was not nearly as bad as it could have been. In the months since then, attention has shifted to ever increasing reports of fraud on Xbox Live.
These account intrusions have come to be known as "FIFA hacks"; although, that is something of a misnomer. Typically, an Xbox Live user will be surprised to receive emails informing him of a large purchase of MS Live points. He will then discover that any balance of points he already had on his GamerTag have been spent. If he is lucky, his password hasn’t been changed, and he will be able to log in to his Windows Live account online, change his password, and regain control of his profile. The less fortunate will discover his password has been changed, his security questions altered, and in some cases, his account transferred to a different country.
In most cases, a call to Xbox Live customer support will be required to have any stolen points refunded, the charges to a credit card or PayPal account reversed, and any other alterations restored. In cases of reported fraud, the customer service representative will inform the customer that the Xbox Live account will need to be "locked" for up to 28 days while the claim is investigated. During that time, no further charges are supposed to be possible, but neither will the user be able to go online with his GamerTag. He can still play games offline and earn Achievements, but they will not be reflected online, nor will he be able to play any multiplayer sessions for nearly a month. Microsoft may even offer a free month of Gold membership to make up for the lost time.
At least, that’s what is supposed to happen.
There are many reports of frustrating, multi-month ordeals faced by Xbox users whose accounts were not properly locked, whose stolen points were never fully refunded, who were forced to dispute the unauthorized charges through their banks when Microsoft support appeared unwilling or unable to rectify the situation, or who lost their accounts for multiple months (if not permanently) because Microsoft claimed to be unable to reverse a region change initiated by the account thief.
Although it’s difficult to forgive the failures in customer service, the seeming surge of account compromises that began last fall appears to have placed considerable stress on Microsoft’s support structure. One common through-line appeared to be activity and downloadable-content (DLC) purchases related to the EA Sports FIFA games. This lead many to speculate that there may be some kind of security breach or fault in Electronic Arts' online profile system that was to blame for the rash of hijackings. In truth, FIFA does not act as the vector for an attack but rather the motivation behind them.
Unlike the PSN intrusion, these Xbox Live hackers are not motivated by a desire to publicly shame Microsoft. Instead, they are purely driven by profit. Prior to last year, there was little money to be made off stolen Xbox Live accounts. A compromised account does not actually reveal enough payment details to be used outside the service, and purchased MS points could not be easily transferred to other GamerTags. That changed when EA introduced a new microtransaction-inspired player trading system and DLC to the FIFA franchise.
 In the game, EA has created a marketplace for players as part of their "Ultimate Team" system. FIFA gamers can spend in-game currency to buy their favorite soccer players to add to their collections or earn coins by selling their own. Serious gamers will spend a lot for the best players available. This would be fine if it was a closed, in-game system, but EA also sells a DLC item that can be purchased over and over again like a pack of baseball cards, which gives the buyer a random chance at a high-value soccer star and other potentially lucrative bonuses. This, coupled with a gray market that has cropped up outside the game where FIFA enthusiasts arrange to buy high-value player cards for real-world money, is where the real trouble begins.
In the game, EA has created a marketplace for players as part of their "Ultimate Team" system. FIFA gamers can spend in-game currency to buy their favorite soccer players to add to their collections or earn coins by selling their own. Serious gamers will spend a lot for the best players available. This would be fine if it was a closed, in-game system, but EA also sells a DLC item that can be purchased over and over again like a pack of baseball cards, which gives the buyer a random chance at a high-value soccer star and other potentially lucrative bonuses. This, coupled with a gray market that has cropped up outside the game where FIFA enthusiasts arrange to buy high-value player cards for real-world money, is where the real trouble begins.
The implication of this type of microtransaction may not be obvious at first, but what the hackers have realized — and what the thousands of "FIFA hack" victims have discovered — is that EA has created a way to launder stolen MS points for real-world cash. Suddenly, there is a significant profit motive to hack random Live accounts that just was not there before. For every account a hacker breaks into, he can buy as many MS points as possible using the payment method already attached to the account, spend as many points as he can on this particular FIFA DLC, and trade all the cards of any value he gets to a dummy GamerTag where they can be held until they are sold through an online auction site. Repeat until the account’s owner notices what is happening or the point purchases will no longer go through, and move on to the next hacked account.
But how are these accounts being compromised in the first place?
It’s important to recognize a few facts before we can speculate on the vector of infiltration. First, the hackers are gaining access to accounts without changing the password. They may decide to change the existing password once they are in to prolong their access to an account, but they always seem to have the original password, which is what they use to access the account in the first place.
Given that fact, we should be able to rule out one class of attack: the "social hack." Typically, social attacks involve targeting specific individuals, gathering personal information through Google and various social networks, and using those details either over the phone with a customer service representative while masquerading as the target or through a website’s password reset mechanism to answer any discoverable challenge questions.
The end goal is to reset an unknown password that was set by the rightful owner of an account to a temporary or new password known only to the hacker. Since the Xbox Live intrusions are occurring without the password being reset, we can discount social attacks as a possible cause. In addition, social hacking is far more time consuming than other types of attacks and usually employed when a hacker has a very specific target. There are prominent examples of celebrities, politicians and other public figures having their email and cellphone accounts invaded and their dirty laundry aired publicly. But it’s not a particularly efficient method for a profit-minded hacker who doesn’t care whose account he accesses and is more interested in turning over as many accounts as he can as quickly as possible.
Another fact we must remember is that enough victims have reported their compromised accounts had unique passwords to cast doubt on another popular theory on how these intrusions are being accomplished. Given the number of other services and sites like PSN, Gawker, or Valve that have had their own systems hacked into and customer information stolen, it is not unreasonable to suspect that hackers are using email addresses and passwords pilfered elsewhere and hoping Xbox Live account holders use the same login credentials on multiple sites. In fact, a few months ago, Sony’s new czar of network security, Philip Reitinger, disclosed that he had detected and blocked just such a mass login attempt against PSN. Sony's network technicians detected this activity as irregular and possibly harmful to PSN users and immediately took measures to protect and inform their customers of the danger.
Unfortunately, it’s a difficult hypothesis to prove, but we have reason to doubt this is a comprehensive explanation. As mentioned above, some victims at least claim to have been using passwords unique to their Live account. From personal experience, I can tell you that the information used to gain unauthorized access to my own account in August did not come from PSN as I did not sign up for PSN until a few months after that intrusion. I can also verify that my information was not contained in the database stolen from Gawker and that the Valve intrusion occurred after my Live account had been hijacked. I know of no other publicized hacks, within the gaming industry or otherwise, that could have exposed my password for Xbox Live.
For many months, Microsoft refrained from commenting officially on the apparent epidemic of account thefts. It was not until a few months ago when a number of prominent gaming journalists found themselves victim to the same fraud and started writing about it for their respective sites did MS release a statement. Officially, Microsoft denies suggestions that the Xbox Live service itself has been hacked and blames "phishing scams" for the so called "FIFA hacks."
Phishing scams essentially involve tricking users into entering their user names and passwords for a service into a fake version of the real site. Typically, someone will receive an email suggesting that there is a problem with his account or promising some kind of freebie that includes a link to a site that looks very official but is actually hosted and controlled by hackers. World of Warcraft is a frequent target for this kind of scam as in-game gold continues to be an asset with real-world value.
It’s not hard to see why Microsoft would blame phishing for incidents of Xbox Live fraud. It’s a known and ongoing problem in the industry, it jives with the fact that the intruders seem to know user passwords, and it conveniently absolves their own security infrastructure of any responsibility. And in truth, phishing is likely responsible for some level of fraud on the service, but it is a leap to suggest it explains all of this latest increase. To many, it appears very much to be a case of Microsoft blaming the victims with a plausible but unverifiable excuse while deflecting attention from a very real, ongoing problem.
And there are many reasons to be skeptical of the official explanation. For one, many people with a high degree of technical knowledge and understanding of good security practices have fallen victim. I can tell you that I personally, emphatically did not fall for a phishing scam. I have never even seen a phishing scam that targets Xbox Live; although, there tends to be one or two WOW scams in my spam folder each week. It’s also difficult to believe Geoff Keighley or Michael Pachter were tricked into signing up for free MS points. Worse than that, if this was a wide spread and incredibly effective phishing scam, where is the evidence? Microsoft offers no proof to support the claim, and we are being asked to believe that not a single person in the gaming press, NeoGAF, 4chan, or SomethingAwful has been wily enough to recognize and document the scam site so many are supposedly victims of? It’s a poor phishing scam that is apparently impossible to find.
All the circumstantial evidence suggests that something else is going on. If these can’t be social attacks, don’t appear to be related to third-party compromises, or entirely caused by phishing sites or emails, then there must be an undisclosed or perhaps undiscovered security flaw allowing hackers to discover user passwords without being noticed. As it just so happens, last week just such a problem was discovered on Xbox.com.
First reported by AnalogHype and Eurogamer, the news comes from an Xbox Live user named Jason Coutee who also recently had his account broken into and had 8000 MS points purchased fraudulently. After contacting Microsoft support, he declined the offer to have his account locked for 30 days so that the intrusion could be investigated. Coutee is employed as a network infrastructure manager and instead decided to conduct his own investigation into the possible cause.
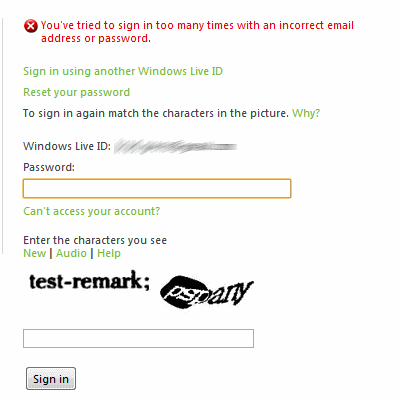 What Coutee discovered was a rather severe flaw in the Xbox.com website login system. For hackers, it’s not difficult to compile a large list of email addresses potentially connected to an Xbox Live gamer tag, and based on the way the site handles errors for nonexistent accounts versus real accounts with incorrect passwords, those can be easily sorted for further scrutiny. But the big problem is the site’s security measures intended to kick in after eight failed password attempts — invoking a CAPTCHA — can be easily circumvented. The whole process can be simply automated by a hacker, which allows him effectively infinite login attempts to to any Live account.
What Coutee discovered was a rather severe flaw in the Xbox.com website login system. For hackers, it’s not difficult to compile a large list of email addresses potentially connected to an Xbox Live gamer tag, and based on the way the site handles errors for nonexistent accounts versus real accounts with incorrect passwords, those can be easily sorted for further scrutiny. But the big problem is the site’s security measures intended to kick in after eight failed password attempts — invoking a CAPTCHA — can be easily circumvented. The whole process can be simply automated by a hacker, which allows him effectively infinite login attempts to to any Live account.
This allows for what are called "brute force" hacks. Essentially, if there is nothing to stop a hacker from trying to log in to a single account as many times as he wants, he can create a script to run through a list of common, stolen, or randomly generated passwords until he finds one that works. Given enough time, hitting the right password for some accounts is inevitable. For this reason, most sites and services will lock an account after a handful of failed attempts. Many also analyze access patterns for such requests in real time to detect and block possibly malicious activity. Unfortunately for hacking victims, Microsoft failed on both accounts.
Now, some will tell you that remotely brute forcing any password that is not a short dictionary word is not feasible, but that belies an antiquated understanding of password security. In order to maximize the possibility of success, hackers have many sophisticated and powerful tools at their disposal. Low-latency, fiber Internet connections, botnets, GPU-accelerated password-cracking software, databases of known passwords from other hacks, and a little human psychology take the hackers a lot further than most suspect. They do not have to test every single possible combination for an eight character alphanumeric password. They can look at the kind of passwords people actually construct and generate a list accordingly.
For a long time, we’ve been told to combine letters and numbers and avoid words to create something secure. Back in 2002, a password like "ronco123" seemed really secure, but computational increases and hacker sophistication have progressed exponentially in the last decade. Now that password is fairly weak. Not as weak as "password" or "1234," but far below current security standards. Furthermore, "ronco123" is constructed in a very obvious manner. The vast majority of people who think they are using good security practices will have a password that looks very similar — if only because it feels natural to put the letters on the left and the numbers on the right. Frequently, the numbers will just be padding, and thus, a lot of 123s or 11s are appended to a word or acronym. Otherwise, you’d expect lots of dates in two or four digits, and given the expected age of your target, you could narrow that further to 01 thorugh 12, 60 thorugh 99, and 1960 thorugh 2012 frequently paired with names of cities, places, or events.
Additionally, there is no reason for a hacker to limit themselves to brute forcing a single account at a time. Let’s assume at a base level that you can’t check more than 100 passwords on a single account per second (although, that is incredibly conservative — in truth, it's probably 10 times that rate). Unless the password in use is exceptionally poor, cracking will still take some time to succeed. The solution is to scale up the scope of the attack by brute forcing many accounts at the same time. Since it can all be automated, there is no reason not to be testing hundreds if not thousands of accounts at the same time for 24 hours a day. Every time a successful password is discovered, it is recorded in a text file for late exploitation. For the hacker, the result is a constant stream of vulnerable accounts that could each pay out hundreds of dollars.
In an official statement given to 1UP when the site reported on the flaw, Microsoft disputed that article’s characterization of this as a "loophole" in their security. According to a Microsoft rep, "The hacking technique outlined is an example of brute-force attacks and is an industry-wide issue." This is true: brute forcing is a known technique, but most organizations have working security measures to prevent it from being an effective attack vector. Microsoft also goes on to reiterate its earlier statements that the service itself has not been hacked, another technical truth. In both cases, Microsoft is playing a semantic game to obfuscate the truth while tacitly acknowledging the critical flaw in their authorization system did exist.
According to a follow up report from Jason Coutee, shortly after the news of this flaw broke, Microsoft implemented a silent fix on the back end of Xbox.com. Hopefully, their solution will be effective in blocking a majority of future attempts to hijack accounts, but their negligence and evasiveness over the FIFA hacks to date are not encouraging. Unless the executives at Microsoft decide to completely change course and come clean with concrete details about what has been going on — something they were eventually forced to do previously with the hardware flaws that led to the Red Ring of Death — we may never have a clear picture of the full extent of the problem.
Tragically, the account hacking itself is only part of the scandal. Even if Microsoft is completely justified in its "blame the user" attitude, it is nonetheless failing quite spectacularly in its duty to safeguard customers against fraudulent transactions. FIFA hacking does not exist on the PS3 for a very specific reason having to do with how each platform handles payment authorizations. Account hacks will always be a problem whether the platform holder is letting the rabble through the front gate or a single user is kidnapped and tortured into giving up his password. For this reason, both PSN and Valve’s Steam store have additional layers of protection against unauthorized purchases.
 When a FIFA hacker logs into an account on Xbox Live, the first thing he will do is to try to initiate a purchase of MS points. No matter where he is or what time it is, as long as there is a payment method attached to the account with an available balance, the charge will go through — no questions asked. Both Steam and PSN handle this potential scenario very differently. If you connect to your PSN account from a new PlayStation 3, PlayStation Portable, or PlayStation Vita, you will not be able to make any purchases through the PlayStation Store unless you reauthorize the saved payment method. This requires again supplying the expiration date and three digit security code for the credit card on record. Valve uses their SteamGuard security, which requires you to enter a code sent to your default email address any time you log into your account from an unrecognized browser or device.
When a FIFA hacker logs into an account on Xbox Live, the first thing he will do is to try to initiate a purchase of MS points. No matter where he is or what time it is, as long as there is a payment method attached to the account with an available balance, the charge will go through — no questions asked. Both Steam and PSN handle this potential scenario very differently. If you connect to your PSN account from a new PlayStation 3, PlayStation Portable, or PlayStation Vita, you will not be able to make any purchases through the PlayStation Store unless you reauthorize the saved payment method. This requires again supplying the expiration date and three digit security code for the credit card on record. Valve uses their SteamGuard security, which requires you to enter a code sent to your default email address any time you log into your account from an unrecognized browser or device.
Both methods are extremely effective at discouraging hackers from targeting those platforms. Even if a password is discoverable, there is no way to easily convert that knowledge to cash without additional information, and if hackers have access to a random user’s credit card details or control over his primary email address, there are far more direct and efficient forms of fraud to indulge in. The most baffling part of the FIFA-hack epidemic is Microsoft’s obstinate refusal to implement these kind of simple, prudent protections to the Xbox Live Marketplace.
Above and beyond how these accounts are accessed or the questionable nature of Microsoft’s customer support for hacked users, that is the biggest question in the whole debacle. Why has Microsoft allowed this rampant fraud to continue for nearly a year without implementing any additional payment protections? They have all the power in this situation. They can even see when a user logs off in California and five minutes later the same account is being used on a 360 in Russia or China to make an unusually large purchase. Ironically, if a credit-card company could see that the transaction was coming from overseas and not Redmond, Washington, the transaction would be flagged immediately as possibly fraudulent and the card frozen. Microsoft cannot plead poverty when Gold membership fees bring in more than a billion dollars of profit each year. To claim it would be too complicated to implement in their legacy system is simply unacceptable.
Continuing as if nothing is wrong or that there is nothing to be done is literally inexcusable. For months, Microsoft has ignored the problem, blamed the victims, denied any responsibility, and refused to make the basic improvements their competitors already employ that would solve the problem completely. Sony is a popular Internet whipping boy thanks to the PSN hack last spring, but despite the sensationalistic reporting and the 77 million accounts exposed, there hasn’t been a single case of fraud connected to the intrusion. In contrast, thousands of paying Xbox Live users every month are losing money to thieves thanks to the lax security and short-sighted policies of Xbox Live.
Please do not take this observation as an attempt to — for lack of a better word — politicize the situation. Too often, already complex and charged events in the industry become even more confused when they become proxy battles in the great fanboy wars. We are not only talking about very different situations but also very different corporate responses. Despite the persistent perception to the contrary, Sony was incredibly forthcoming about the attack they suffered. It took only a few days to go from initial detection to a very thorough public disclosure where Sony took full responsibility.
And while their security was actually up to industry standards (despite rumors to the contrary), they made the hard choice to bring the entire network down long enough to thoroughly investigate the attack and overhaul their internal procedures. This was at great expense to themselves and their partners, especially those who depended on revenue from digital sales through PSN. For every customer of the free service, they offered identity protection on the chance it would be necessary and as many as four free games.
Sony’s humility and contrition is in stark contrast to Microsoft's arrogant dismissals, manipulative statements, and attempts to evade responsibility. This should not be a Sony versus Microsoft issue mired under the din of ill-informed partisans repeating ignorance as fact in a misguided attempt to glorify their preferred platform at a competitor’s expense. Sony did the best they could in a difficult situation to do right by their customers. We should expect no less from Microsoft, and if they will not make the same effort, holding their feet to the fire is the appropriate response.
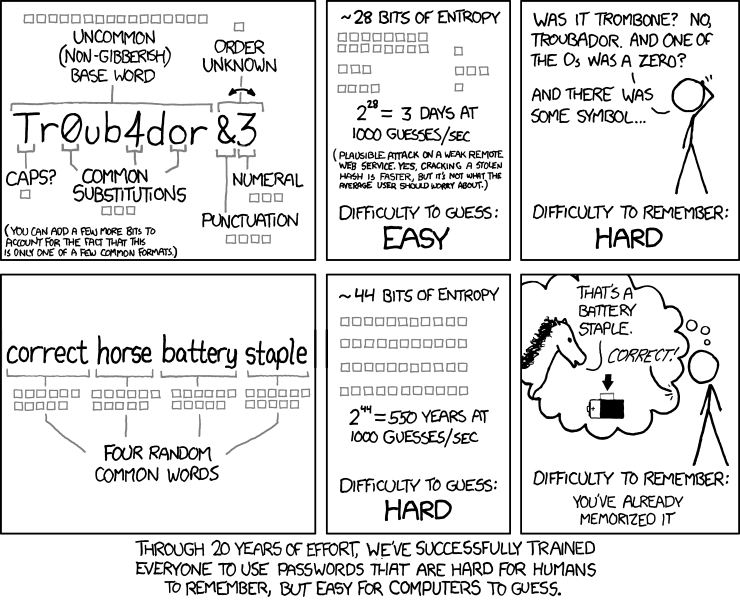
Sadly, if Microsoft will do nothing, it falls to the users to protect themselves. Xbox.com has a list of recommended security guidelines for users to follow. Others recommend removing any payment options associated with your account. But the most important thing now is to make sure your Live password is unique and very long. Eight or nine character passwords are no longer sufficient. As a recent XKCD comic points out, a 20-character password you can remember is far more secure than an eight-character password that uses a random combination of letters, numbers, cases, and special symbols. Tell your friends, tell your family. After all, we live in trying times.