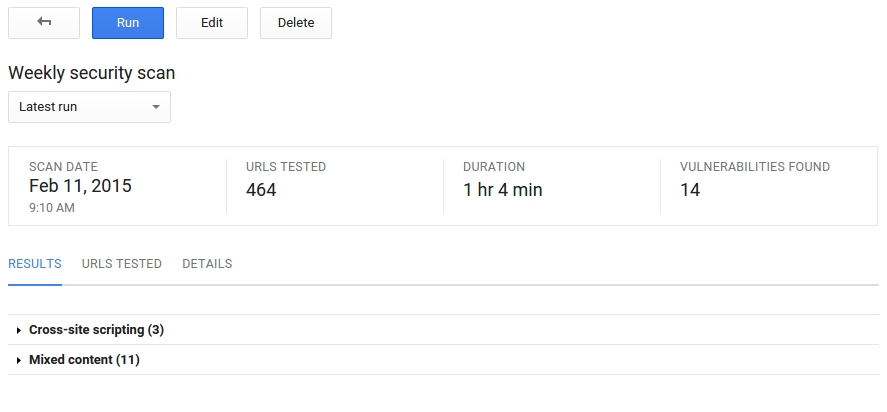
Google today launched the Google Cloud Security Scanner in beta. The new tool lets App Engine developers scan their web applications for two common types of vulnerabilities: cross-site scripting (XSS) and mixed content.
To access Google Cloud Security Scanner, head to the Google Developers Console, select Compute, choose App Engine, and then Security. This will run your first scan.
Here is the tool’s official description:
It crawls your application, following all links within the scope of your starting URLs, and attempts to exercise as many user inputs and event handlers as possible. Only regular App Engine instances are supported. You cannot use the Security Scanner with App Engine Managed VMs, Google Compute Engine, or any other resources.
The scanner works by first making a high-speed pass, crawling and parsing the HTML, and then executing a slow and thorough full-page render to find the more complex sections of a site. In other words, it uses a multi-stage pipeline to test HTML5 and JavaScript-heavy apps that often feature rich multi-step user interfaces.
Google notes that there are two typical approaches to such security scans:
- Parse the HTML and emulate a browser. This is fast; however, it comes at the cost of missing site actions that require a full DOM or complex JavaScript operations.
- Use a real browser. This approach avoids the parser coverage gap and most closely simulates the site experience. However, it can be slow due to event firing, dynamic execution, and time needed for the DOM to settle.
Using Google Compute Engine, Google’s method is to dynamically create a botnet of hundreds of virtual Chrome workers to scan an app. Target sites won’t be overloaded, however, as each scan is limited to a maximum of 20 requests per second.
The site is then attacked again to test for XSS via a benign payload that relies on Chrome DevTools to execute the debugger. If the debugger fires, Google considers this to be JavaScript code execution. The company claims that “false positives are (almost) non-existent.”
This approach is hardly thorough, but it is a low-effort and low-noise way to check for security issues. That said, Google still recommends “a manual security review by your friendly web app security professional.”
As for Cloud Security Scanner, Google doesn’t say how long the service will be in beta. It does, however, promise “many more features to come.”