Open-source software has one big flaw: While a company might have a team of developers, they don’t actually know who built their software.
“People that develop software nowadays don’t write it; they assemble it,” said E. Wayne Jackson III, the chief executive of open-source compliance company Sonatype in an interview with VentureBeat. “This move to a Lego-based model of software assembly has been completely transformative in how productive we are. … It’s kind of like mobility. These really powerful handheld devices are incredible in a good way but we’re learning other things about them that we need to be concerned about.”
While you might know the developers who built your program, you might not know the many developers who actually built the components that went into that software. You’ve never met them. They’re not on your payroll. They could be anyone.
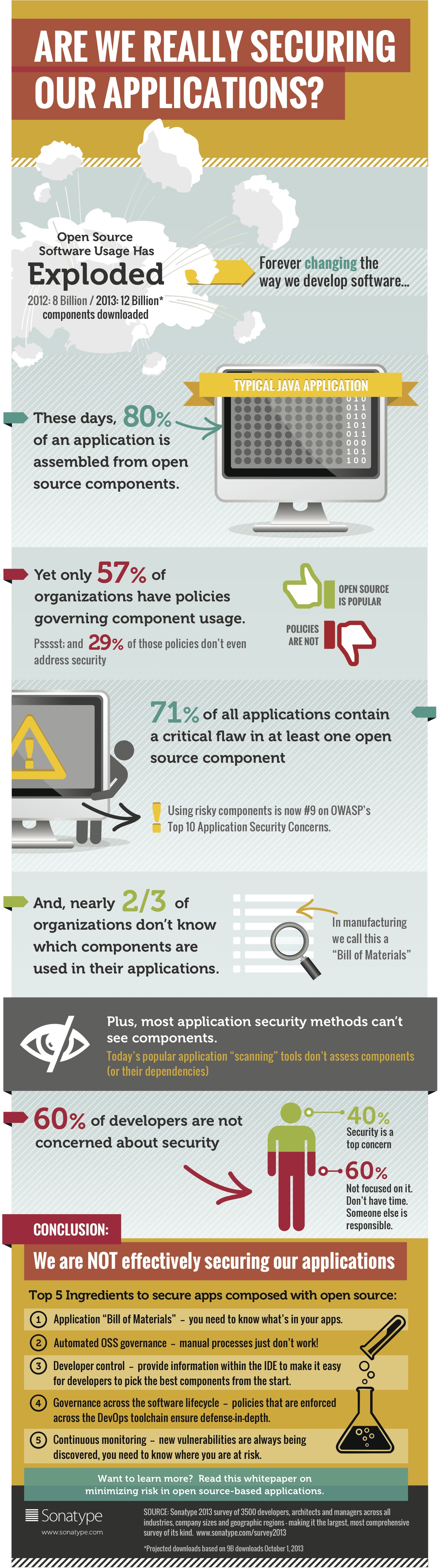
Open-source components are the smaller pieces of software that help build your bigger program. They’re available online, and anyone can use them or change them. Now, 71 percent of applications have a security flaw in them due to a flaw in an open-source component, according to Sonatype’s 2013 survey of 3,500 developers.
For this reason, Jackson spoke to the White House about why this is such a big deal. He half-joked that government applications could have partially been built by China and North Korea because people don’t think to check the “provenance” of their components.
“I’ll pick on HealthCare.gov,” said Jackson. “We don’t know who wrote the components for the HealthCare.gov. We don’t know if it was an enemy nation state. People tend to use open-source just assuming ‘everybody else does.'”
Jackson stressed that he doesn’t intend this to be a mark against open-source. In fact, he says that open-source is too ubiquitous to not use. At the time of the study, Sonatype projected that people would download 12 billion pieces of open-source software in 2013. That’s a 50 percent increase from the 8 billion in 2012.
Instead of dumping open-source, Jackson suggests the following tips for keeping your component safe:
- Make sure that anyone who can play with the code of an open-source project provides identification. The Eclipse Foundation, according to Jackson, is a good example of using this best practice. It requires a signature on an intellectual property release form.
- Make sure the open-source component you’re using has been digitally signed. That way there is more accountability in knowing who built the software.
- Keep and maintain a “Bill of Materials,” or list of all the software components you use in a project and routinely analyze it for security updates.
- Make sure your developers are using a secure platform to build on.
But developers still need to be able to do their jobs quickly and easily, so Jackson further suggests creating a rating system by which developers judge the risk associated with a component and whether or not to use it.
“Define a set of project best practices and a scoring system so as people make decisions about the software that they’re using they can have a very real number to understand what the potential risks are for using that slice of open-source,” he explained.
Companies like Black Duck, Jackson’s Sonatype, and Coverity provide tools to help automate this process.
Open-source software has done a lot to move the development industry itself forward, and you shouldn’t fear it. Companies now just need to know how to handle these new tools and quit letting Joe Schmo build their critical applications for them.
Check out the infographic below for more stats about open source today:
VentureBeat's mission is to be a digital town square for technical decision-makers to gain knowledge about transformative enterprise technology and transact. Learn More
![Reblog this post [with Zemanta]](http://img.zemanta.com/reblog_e.png?x-id=ab22fea6-fdf2-4b3d-9fe1-0fd356223358)
