It’s time to add another issue to the list of what’s ailing publisher Electronic Arts. The company’s chief executive officer announced yesterday that he is stepping down, and it is still reeling from a public-relations snafu with the recently launched city-builder SimCity. Now, a security research firm revealed that members of EA’s digital-download service are vulnerable to attack from hackers.
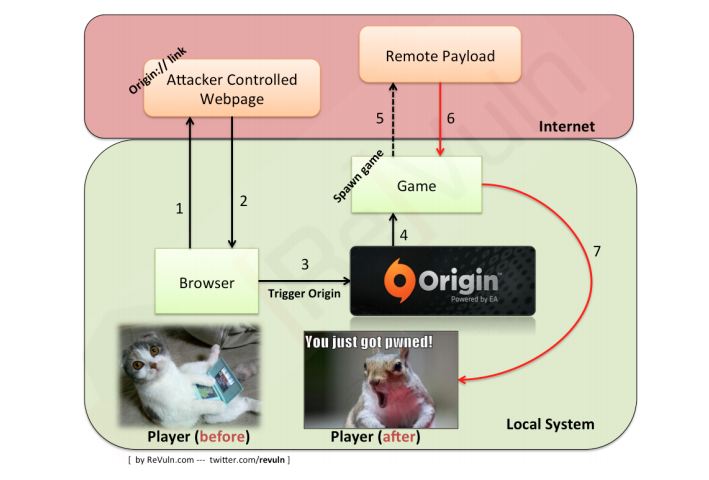
[aditude-amp id="flyingcarpet" targeting='{"env":"staging","page_type":"article","post_id":702136,"post_type":"story","post_chan":"none","tags":null,"ai":false,"category":"none","all_categories":"games,","session":"C"}']A fatal flaw in EA’s Origin service may enable hackers to remotely execute software on a target’s Mac or PC, according to Malta-based security researchers ReVuln (via Time’s Techland blog). ReVuln published a paper earlier this month that explains the vulnerability in detail.
“Our team is constantly investigating hypotheticals like this one as we continually update our security infrastructure,” Origin spokesperson John Reseburg told GamesBeat.
The hack only takes seconds. It works by exploiting an “Origin://link” uniform resource identifier (URI), which publishers utilize to enable browsers to open and control actions on the Origin platform. Origin’s links follow a particular pattern. Hackers can mess around with that pattern to make the URI execute different commands. One of those commands could be bringing up a box that asks a user to download an application. They might trust that application because they’re on their trusted Origin site and click yes. The malware will then install, and the hacker will effectively “own” the system.
“Using games as an attack vector is pretty difficult to spot,” ReVuln security researcher Donato Ferrante told GamesBeat. “One of the reasons is that most people underestimate games as a possible way for attackers to compromise their systems.”
ReVuln released a proof of concept of the hack, which you can see in the video embedded into ReVuln’s Tweet:
EA Origin Insecurity paper: http://t.co/2OexmmoYur and video: http://t.co/b0EnqEktwt #BlackHatEU #0day
— REVULN (@REVULN) March 15, 2013
In October, ReVuln discovered a similar insecurity in Valve’s Steam digital service — EA’s primary competitor in the PC space. Ferrante claims Valve still hasn’t addressed the issue.
The security firm suggests that users set their browsers to pop up with a prompt when attempting to open a game in Origin or in Steam. More security-conscious users can install a tool like URIprotocolview to disable the “Origin://” URI.
[aditude-amp id="medium1" targeting='{"env":"staging","page_type":"article","post_id":702136,"post_type":"story","post_chan":"none","tags":null,"ai":false,"category":"none","all_categories":"games,","session":"C"}']
VentureBeat security reporter Meghan Kelly contributed to this report