Attacking smartphones with malware is to become a profitable business in 2012, according to a report by Lookout Mobile Security. Criminals took an estimated $1 million from Android owners this year, and the threat is only getting bigger.
“Bad guys will always follow the money, and with the meteoric growth of mobile devices there is more money to be made in mobile fraud than ever before,” the company said in a blog post.
It has taken mobile malware writers two years to accomplish what took many over 15 years on the PC, according to Lookout’s chief technology officer Kevin Mahaffey. Mobile is, in essence, the new frontier for people who make money through cyber attacks, and their efforts aren’t going to waste. The Android operating system continues to be a target for mobile malware. Users can expect to encounter attacks four percent of the time, a three percent increase from 2011’s prediction. Web browsing is also becoming a big threat, with 38 percent of Android owners encountering a malicious link — 40 percent if you only consider the United States.
So what exactly is infecting our phones? More cases of smartphone-specific SMS fraud are arriving in the marketplace. But many of these attacks have similarities to PC counterparts. For instance, botnets, malicious advertising and web browser links are becoming more of an issue for mobile devices.
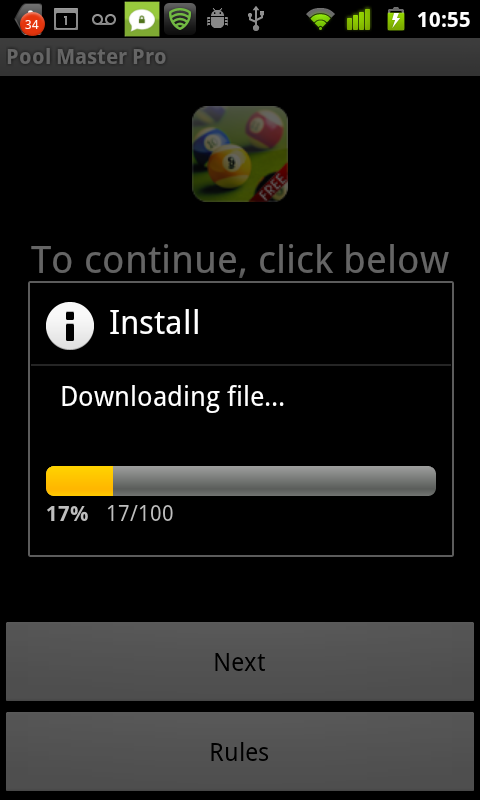 SMS fraud allows a criminal to take over your phone’s messaging permissions to send and receive text messages to a “premium rate number.” Every time the number is used, that malware writer can charge you money. Some instances saw charges of up to $9.99 with the GGTracker Android infection, an attack that focused on US users. More recently, the RuFraud scam was identified. This attacked mostly Eastern European users who downloaded an app skinned to look like a horoscope, Twilight wall paper app, or free versions of popular games such as Angry Birds. When the person clicked through the initial start screen, they “agreed” (see photo right) to a terms of service clause that allowed the app to take over messaging privileges. The ToS was less than legitimate, however, and buried under links so users could not find it. Google removed 22 applications with the RuFraud scam inserted. Lookout expects that a few infected apps will re-enter the marketplace every few days.
SMS fraud allows a criminal to take over your phone’s messaging permissions to send and receive text messages to a “premium rate number.” Every time the number is used, that malware writer can charge you money. Some instances saw charges of up to $9.99 with the GGTracker Android infection, an attack that focused on US users. More recently, the RuFraud scam was identified. This attacked mostly Eastern European users who downloaded an app skinned to look like a horoscope, Twilight wall paper app, or free versions of popular games such as Angry Birds. When the person clicked through the initial start screen, they “agreed” (see photo right) to a terms of service clause that allowed the app to take over messaging privileges. The ToS was less than legitimate, however, and buried under links so users could not find it. Google removed 22 applications with the RuFraud scam inserted. Lookout expects that a few infected apps will re-enter the marketplace every few days.
Botnets, or a series of interconnected mobile phones that can work together to infect other phones on a large scale have been found. These have not, however, been used to their full potential. Attacks such as Geinimi, which originated out of China, have the ability to take over your phone after receiving commands from a remote server, according to Lookout. They can take your information and can attempt to infect other phones from your own.
Malicious advertising and web links are most similar to their PC counterparts. In order to become affected by malware, a smartphone user must simply click an infected link or advertisement that takes them to a malware website. This is where Apple’s usually protective iOS is actually put at risk. Jailbreaking is not uncommon with the iPhone and many people use jailbroken phones for interesting hacks intended for personal use, not for malicious attacks. For instance, some break into their iPhones to create interesting uses for the Siri application, run different carriers’ services, or port incompatible apps to older operating systems. Some of these jailbreaking websites, however, come with malware that piggy backs onto your newly vulnerable phone.
In-app advertising doesn’t come out unscathed either, with some “malvertisements” popping up right in the app itself.
There are new ways to speed up the process, which can save a malware writer time and money, and new mobile vulnerabilities to exploit. As in any business, the less money you spend on operating costs, the more you get to keep when the revenue starts pouring in. Mobile criminals want to find new, faster, cheaper ways of distributing their malware, and have seemingly figured out a way to automate the “packaging” process. That is, a criminal takes legitimate, existing applications and re-packs them with new mobile malware. The app still looks legitimate, but has picked up a malware hitchhiker. Lookout Mobile is seeing the rapid repackaging of apps exceed rates that are possible when done manually. Some repackaging attempts have been successfully completed in only seconds, thus criminals must have developed a technology to allow them to do this faster.
The other issue with the mobile operating system is the time it takes to update vulnerabilities. Sending patches out to the OS takes time, which means criminals can wring a vulnerability dry before a fix ever arrives.
Apps that are most likely to come with these mobile attacks are gaming, utility (such as flashlights and battery saver apps), and porn applications. Be careful when downloading these, particularly if you are downloading them from third-party app stores such as GetJar. According to Lookout Mobile, these third-party marketplaces are where malware writers try out their new tricks.
As we always advise, be careful what you click — particularly if you are an Android user — and keep a discerning eye in 2012.
[Android image via Shutterstock]
VentureBeat's mission is to be a digital town square for technical decision-makers to gain knowledge about transformative enterprise technology and transact. Learn More


