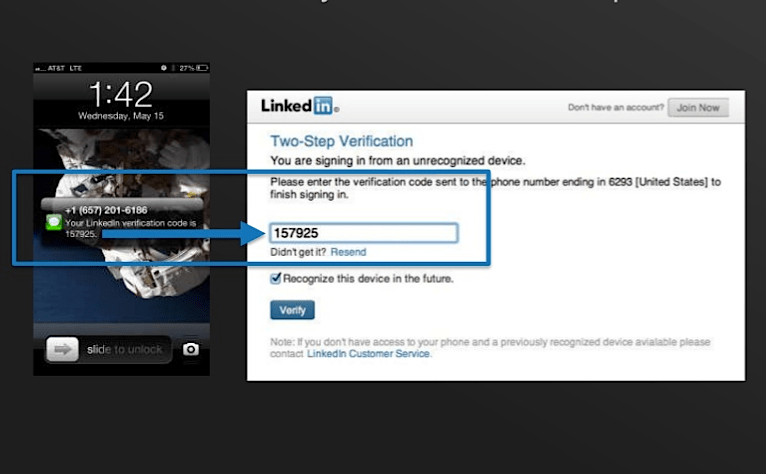
LinkedIn added two-factor authentication to its login process today, which isn’t a surprise at all. It and a handful of big-name tech companies are adding the security feature that is quickly becoming a buzzword in the industry.
[aditude-amp id="flyingcarpet" targeting='{"env":"staging","page_type":"article","post_id":748559,"post_type":"story","post_chan":"none","tags":null,"ai":false,"category":"none","all_categories":"security,","session":"C"}']Two-factor authentication is a more secure means of proving your identity to a company’s server than the traditional username and password combination. In most cases, two-factor authentication requires the input of a temporary code, which is provided to you either through an app like Google Authenticator, an SMS message, or through a dongle, such as RSA’s tokens. LinkedIn will provide these codes through SMS messages.
“We think LinkedIn is taking a pragmatic approach given the current authentication options available in the marketplace,” said Jamie Cowper, a senior director at Nok Nok Labs, in an email to VentureBeat, “Large-scale sites like LinkedIn need to see SMS as the first step in a broader multi-factor strategy that supports users with different devices and needs.”
AI Weekly
The must-read newsletter for AI and Big Data industry written by Khari Johnson, Kyle Wiggers, and Seth Colaner.
Included with VentureBeat Insider and VentureBeat VIP memberships.
The traditional login approach of username and password — a secret that is supposed to be shared between only you and a company’s servers — is prone to failure, so two-factor adds in another barrier to entry for hackers … and, unfortunately, users too.
In the past few months alone it seems companies who recently made headlines for hacks have rolled out two-factor authentication. Apple, Twitter, Evernote, Microsoft all fall into this category. In June 2012, hackers breached LinkedIn, stealing millions of passwords. It was a blow to the community, and having two-factor authentication certainly adds an extra feeling of security. But we need to make sure we’re not putting two-factor up on too high of a pedestal.
There are a couple of ways two-factor authentication can fail. First is simply that “barrier to entry” we talked about before. If people feel like it’s too much of a hassle to pull out their phone or a special piece of hardware to log into their accounts every day — or if they get locked out of their accounts too frequently — then they simply won’t use it. Sure that’s not a technical failure of two-factor, but it is a failure in design.
Second, two-factor authentication won’t protect you from phishing attacks. As security reporter Brian Krebs explains, consumer sites often leave these codes “active” for longer than is advised because they don’t want to create that barrier to entry. Thus, the same code may be accessible for hours instead of seconds. If a hacker set up a phishing scam to steal your information, they could theoretically phish one of these codes out of you alongside your username and password.
“We think the market will come to the realization that much more will have to be done to address current authentication issues,” said Cowper. “We expect to see the enthusiasm for SMS two-factor authentication to dim and the adoption of more innovative approaches in the future.”
Two-factor is definitely a help and, yes, is better than nothing. But let’s make sure not to call it our saving grace lest we be seriously disappointed when it fails.
[aditude-amp id="medium1" targeting='{"env":"staging","page_type":"article","post_id":748559,"post_type":"story","post_chan":"none","tags":null,"ai":false,"category":"none","all_categories":"security,","session":"C"}']
VentureBeat's mission is to be a digital town square for technical decision-makers to gain knowledge about transformative enterprise technology and transact. Learn More