Want smarter insights in your inbox? Sign up for our weekly newsletters to get only what matters to enterprise AI, data, and security leaders. Subscribe Now
Researchers at SentinelOne‘s SentinelLabs today disclosed five critical vulnerabilities in Microsoft Azure Defender for IoT.
The vulnerabilities have a severity score as high as 10.0, SentinelLabs said.
“[A] successful attack may lead to full network compromise, since Azure Defender For IoT is configured to have a TAP (Terminal Access Point) on the network traffic,” the researchers said in a SentinelLabs blog post. “Access to sensitive information on the network could open a number of sophisticated attacking scenarios that could be difficult or impossible to detect.”
The vulnerabilities affect both cloud and on-premises customers, the researchers said, and are being tracked at the following CVE (Common Vulnerabilities and Exposures) numbers:
AI Scaling Hits Its Limits
Power caps, rising token costs, and inference delays are reshaping enterprise AI. Join our exclusive salon to discover how top teams are:
- Turning energy into a strategic advantage
- Architecting efficient inference for real throughput gains
- Unlocking competitive ROI with sustainable AI systems
Secure your spot to stay ahead: https://bit.ly/4mwGngO
- CVE-2021-42310
- CVE-2021-42312
- CVE-2021-37222
- CVE-2021-42313
- CVE-2021-42311
SentinelLabs says it reported its findings to Microsoft last June.
“Microsoft has released security updates to address these critical vulnerabilities,” the researchers said in the blog post. “Users are encouraged to take action immediately.”
SentinelLabs says it hasn’t found evidence of the vulnerabilities being exploited in the wild.
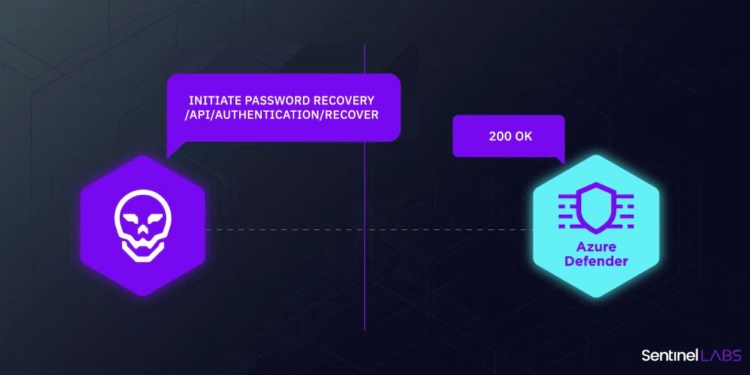
The vulnerabilities affect the service’s password reset mechanism, and “can be abused by remote attackers to gain unauthorized access,” the researchers said.
Additionally, “multiple SQL injection vulnerabilities in Defender for IoT [can] allow remote attackers to gain access without authentication,” the blog post says.
In a statement provided to VentureBeat, Microsoft said that “security vulnerabilities are serious issues we all face and that is why we partner with the industry and follow the Coordinated Vulnerability Disclosure (CVD) process to protect customers before vulnerabilities are public.”
“We addressed the specific issues mentioned and we appreciate the finder working with us to ensure customers remain safe,” Microsoft said in the statement.
Microsoft Defender for IoT is an agentless security solution for IoT and operational technology (OT) assets. The solution includes continuous IoT/OT asset discovery, threat detection and vulnerability management.
Given that Defender for IoT is a security product itself, SentinelLabs says that is research “raises serious questions about the security of security products themselves and their overall effect on the security posture of vulnerable sectors.”