LAS VEGAS — You downloaded an app from a third-party marketplace you don’t trust. Sure, the app might function like it’s supposed to, but it might have just turned your phone into a stealthy spy machine.
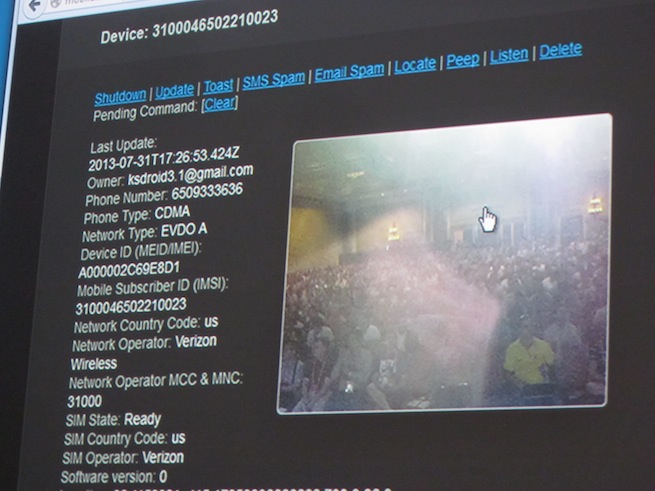
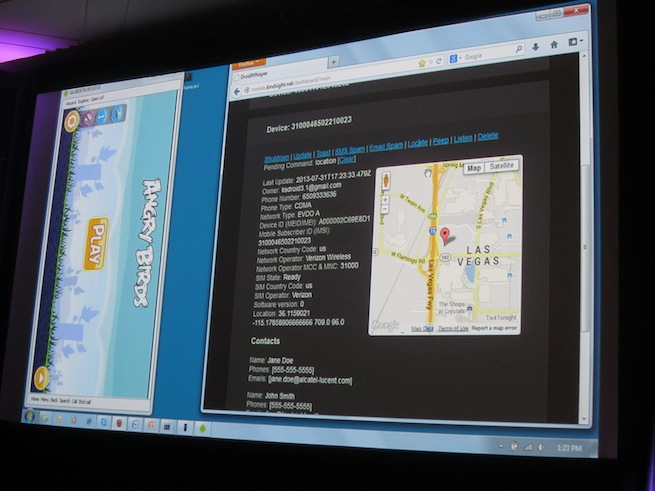 You’ve heard not to download apps from third-party stores, but what’s malware really going to do, anyway? Steal your device information? That’s not that bad. Except for when your phone starts silently taking pictures of you, recording your conversations, downloading your contact list, and sending maps of your location to hackers.
You’ve heard not to download apps from third-party stores, but what’s malware really going to do, anyway? Steal your device information? That’s not that bad. Except for when your phone starts silently taking pictures of you, recording your conversations, downloading your contact list, and sending maps of your location to hackers.
No, this isn’t a nation state attack. This malicious app called DroidWhisperer was built by Kindsight security researcher Kevin McNamee, and for those in the industry, it seems fairly easy to do make such malware. He modeled the app after Angry Birds and submitted to a third-party app store. Once someone downloads the app, it connects the entire phone over the Internet to a command-and-control server.
What the hacker sees is both scary and impressively simple. A small dashboard shows different devices connected to the C&C through the app. He can click on a target phone and data such as the phone number, e-mail address, contact list, unique identifier, and carrier pop up immediately.
At the top of the dashboard there are different action buttons to take a picture, record video and audio, and send text messages and push notifications (think of the scary scene in Ghost when Patrick Swayze possesses a computer and writes “murder murder murder” on the screen).
 “We’re using the standard APIs that Android provides,” said McNamee at the Black Hat conference. “It makes the perfect platform for spying.”
“We’re using the standard APIs that Android provides,” said McNamee at the Black Hat conference. “It makes the perfect platform for spying.”
And stealthy it is. In order to hide his actions, McNamee first built-in the capability to turn down the phone’s volume so you don’t hear the phone performing different actions, such as the click of a camera. When it comes to taking pictures and video, the iPhone always shows a preview of this content. So he told the phone to display this information as only one pixel — too tiny for anyone to notice.
The app itself also functions just like Angry Birds, so no one would suspect its real purpose. He did this by downloading the legitimate Angry Birds and looking at the “APK” file, or the application package file, which houses all the information about the app. He then took apart the Angry Birds app, keeping all the parts, but slipping in his own code where appropriate and then putting it back together.
“It is a very powerful sort of cyber-surveillance device, the phone,” said McNamee. “Android is a very flexible platform to work with … I believe the same thing can be done with iOS.”


